- Products & services Products & services
- Resources Resources
- Community CommunityDiscussion
- Discussion
- Knowledge
- IdentityIQ wiki Discover crowd sourced information or share your expertise
- IdentityNow wiki Discover crowd sourced information or share your expertise
- File Access Manager wiki Discover crowd sourced information or share your expertise
- Submit an idea Get writing tips curated by SailPoint product managers
Knowledge
- Compass
- :
- Products
- :
- File Access Manager
- :
- File Access Manager Wiki
- :
- File Access Manager Component Overview
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
File Access Manager Component Overview
File Access Manager Component Overview
- IdentityIQ File Access Manager Components and Services
- Example Deployment Models
- Systems Monitored by File Access Manager
- Simple Deployment
- Distributed Deployment Model
- Elasticsearch
- SQL Server Database
- File Access Manager Services
- Core Services
- Central Services
- Agents
- Other Services
IdentityIQ File Access Manager Components and Services
File Access Manager is a componentized solution that is made up of distributed Windows services, a search engine, and a central database. This componentized structure gives you the flexibility to scale, load balance, support firewalls, et cetera, but also means that there is no single architecture/deployment model that is the right solution for every implementation.
Some services are always installed in the central installation site, co-located with the system’s central database. Others services may be installed centrally, or in a remote server location closer to the systems from which they are collecting data.
Understanding the functions of each service and component, and the connectivity and communication requirements for each of them, can help you plan your implementation for best performance.
Example Deployment Models
This section shows you some example deployment models for both a simple deployment, and a distributed deployment. Each of the components and services in the diagrams is described in more detail below.
Systems Monitored by File Access Manager
Note that the deployment diagrams below include systems outside of File Access Manager:
- Target Applications are all the places you may have sensitive data stored, such as file shares, collaboration portals, mail systems, et cetera. The target applications are also the sources from which File Access Manager gathers information about the permissions your users have on your data. In addition, the target applications are where activity monitoring (that is, who is actually accessing your data, and what are they doing) is focused. These target applications are also sometimes referred to as endpoints.
- Identity Stores provide fuller information about who your users are, and what groups exist in your organization; for example Active Directory, Azure, and NIS. Information gathered from identity store enriches the information gathered from your target applications, by providing more information about the users and groups that have permissions on your data.
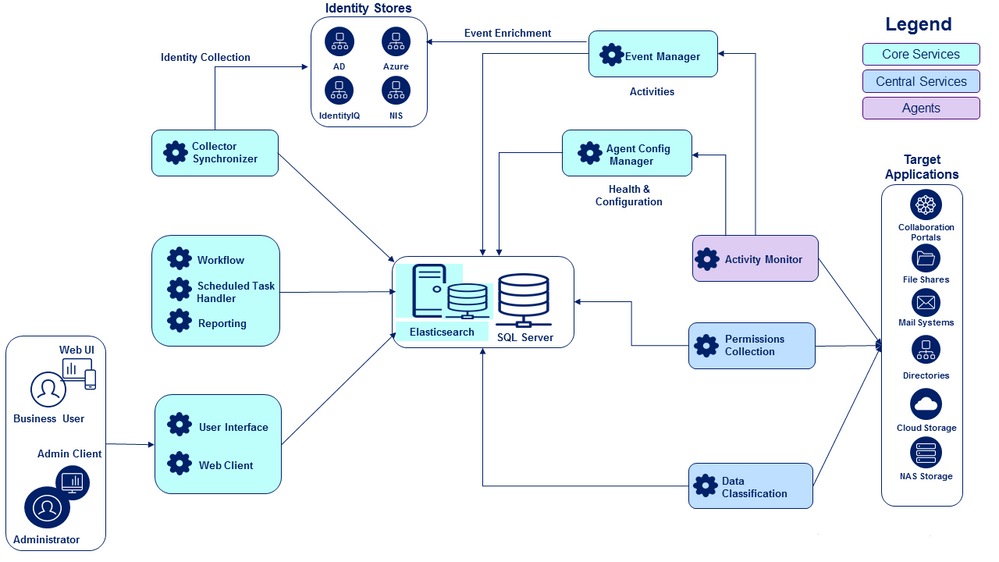
Simple Deployment
A simple deployment is one in which there is a single data center (physical location) for both the central File Access Manager installation and the target applications and identity stores it communicates with. In this diagram, note in particular the simple deployment structure for Permissions Collection and Data Classification.
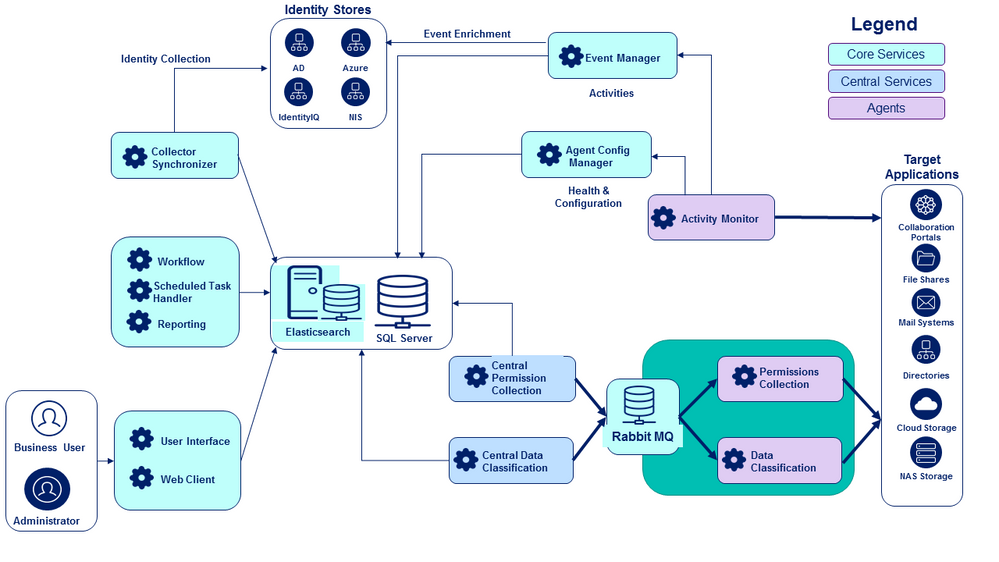
Distributed Deployment Model
A distributed deployment model is used in environments with multiple data centers, where the target applications may be physically located far from the central installation site. In this scenario, network performance must be taken into consideration in the deployment architecture. Note the difference in deployment structure for Permissions Collection and Data Classification, as compared to the simple example shown above.
The sections below describe the File Access Manager database, components and services in more detail.
Elasticsearch
Elasticsearch is a Lucene-based search engine and data store that is optimized for text searches. IdentityIQ File Access Manager uses Elasticsearch to store and query activity data. Elasticsearch is installed as part of the File Access Manager installation process.
SQL Server Database
File Access Manager uses a SQL Server database for maintaining File Access Manager information, and as a backup for the Elasticsearch data store. A SQL Server instance, in a supported version and with sufficient resources, must be installed at the central installation site as a prerequisite to installing File Access Manager; the File Access Manager installation creates the required database in SQL Server. SailPoint strongly recommends a dedicated SQL Server instance for File Access Manager.
File Access Manager Services
The services that make up File Access Manager can be categorized into core services, central services, and agents. There are a few additional, optional services that may be release-specific (that is, not every service is included in every release); these are briefly described at the end of this section.
Core Services
These are services which are essential to fundamental File Access Manager operations, and which also must, for performance reasons, be located in the central File Access Manager installation site, close to the SQL Server database.
The core services are:
| Service Name | Description | Functions |
| Agent Configuration Manager | Communicates with the Activity Monitors, Permission Collectors, and Data Classification Collectors to receive health checks and provide configurations. It is also the entry point for the installation process of Activity Monitors and Collectors. |
Activity Monitoring |
| Collector Synchronizer | Performs Identity Collection and the Access Fulfillment tasks | Identity Collection Access Fulfillment |
| Elasticsearch | This full text indexing search engine and data store retains all data on activities collected by the Event Manager. | Activity Monitoring Threshold Based Alerts |
| Event Manager | Responsible for getting activities from the Activity Monitors, enriching data, evaluating alert and discard rules, and saving activities to the database and to Elasticsearch. | Activity Monitoring Real-time Alerts Threshold Based Alerts |
| RabbitMQ |
This service is a secure message broker for communication between the Central Permissions Collector and Central Data Classification services, to/from the Permissions and Data Classification Collector agents. Note that while Rabbit MQ is considered a core service, it is required only if you choose to implement your Permission Collection and Data Classification components in a split central service engine/remote collector agent configuration, as described in the Central Services section, below. |
Permissions Collection Data Classification |
| Reporting | Generates all reports. | Reporting |
| Scheduled Task Handler | Schedules and dispatches scheduled tasks when they are due, and runs all maintenance tasks. | Schedule Tasks DB Cleanup task Events Deletion task Events Re-Indexing task Application Deletion task Periodic Elasticsearch & RabbitMQ health checks |
| User Interface | Responsible for communication with the IdentityIQ File Access Manager Admin Client. | |
| Web Client | File Access Manager web interface | |
| Workflow |
Manages the creation of access review campaigns (to certify user and group access to sensitive data), and management of review processes. |
Access Certification Campaigns Access Requests Business Asset Compliance |
Central Services
These are services which are essential to fundamental File Access Manager operations, but whose configuration and location will depend on the specifics of your implementation.
The central services are:
| Service Name | Description | Functions |
| Central Permissions Collector |
In a simple architecture, it connects to the target applications and collects resources and permissions data. In a distributed architecture, it aggregates permissions data received from collector agents through the message broker. |
Crawling Permissions Collection |
| Central Data Classification |
In a simple architecture, it connects to the target applications and classifies sensitive files based on the data classification policies you define. In a distributed architecture, it aggregates classification data received from collector agents through the message broker. In cloud environments specifically (such as a Box drive), the collectors copy resources to the server where the collector agent is installed, where the data is then classified; classification data is then sent via the message broker to the central Data Classification engine. Once classification data has been collected, the local copies of the resources are discarded. |
Data Classification |
The Permissions Collection and Data Classification services can be deployed in one of two ways:
- As single services that reside with the central File Access Manager installation. This implementation is best suited for simple architectures, where latency between the central File Access Manager installation and the various endpoints you are monitoring is not expected to hinder performance. (Note however that even in simple architectures, the volume of data to be processed can be a factor in deciding how to implement the Permissions Collector and Data Classification services; if you have large volumes of resources to process, implementing multiple collectors can help you process them more efficiently through parallelization.)
- As a split central “engine” and remote worker agent “collector” services, with a main engine for each of the services (a Central Permissions Collection and a Central Data Classification) located in the central File Access Manager installation site, and individual Permission Collection and Data Classification agents installed near the endpoints they interact with. This implementation is best suited for a distributed architecture, where some endpoints may be located far from the central File Access Manager site, in hybrid cloud/on-premise environments, or in large-scale environments with a significant number of endpoints. For this configuration, you must also install the RabbitMQ service to act as a message broker between the central “engine” services and the agent “collector” services. It is recommended that the Rabbit MQ be installed in the central File Access Manager site.
Agents
Some File Access Manager components are categorized as Agents. They differ from the services described above in that the optimal location for installing them will depend on the specifics of your topography, in particular where your monitored endpoints are located, and how you choose to deploy the Permissions Collection and Data Classification modules. Additionally, these agents do not have direct access to the File Access Manager data stores located in the central site.
These are the File Access Manager agents:
- Activity Monitor (Activity Monitors monitor and collect events from an application. Each application type has a specific activity monitor designed to monitor it.)
- Permissions Collection (when configured to pair with a Central Permissions Collector engine)
- Data Classification (when configured to pair with a Central Data Classification engine)
The number and location of Activity Monitors you install will depend on how many endpoints you are monitoring. In general, you will need one Activity Monitor per endpoint (for example, one for each NetApp File Server and others for each SharePoint site, et cetera), and they should be installed within the same site/subnet as the endpoint.
Other Services
File Access Manager can include other optional services. These are discussed in more detail in the SecurityIQ Administrators Guide. They include:
- Business Asset Compliance: Creates and manages Compliance Controls.
- Crowd Analyzer: Creates and manages data owners’ election goals.
- Oracle Segregation of Duties: Separation of duties policies for Oracle endpoints.
- SAP Segregation of Duties: Separation of duties policies for SAP endpoints.
- WatchDog: Monitors the status of most other File Access Manager services, allows administrators to start, stop, and restart them through the Admin Console’s Health Center, and manages upgrade deployment process.
Most of these services are installed centrally like the Core services. The only exception is the WatchDog service. A Watchdog Service instance is automatically installed on every File Access Manager server where the services it monitors are installed.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Segregation of duties using the Oracle and SAP connectors are no longer supported, as of June 2019
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Can this doc be updated. It seems that as of 8.4 rabbitmq is a required component. Also can you explain the communication between activity monitors and event collectors.