- Products & services Products & services
- Resources ResourcesLearning
- Learning
- Identity University Get technical training to ensure a successful implementation
- Training paths Follow a role-based or product-based training path
- SailPoint professional certifications & credentials Advance your career or validate your identity security knowledge
- Training onboarding guide Make of the most of training with our step-by-step guide
- Training FAQs Find answers to common training questions
- Community Community
- Compass
- :
- Discuss
- :
- Community Wiki
- :
- IdentityIQ Wiki
- :
- IdentityIQ 8.0: File attachments in access requests
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
IdentityIQ 8.0: File attachments in access requests
IdentityIQ 8.0: File attachments in access requests
Back to the IdentityIQ 8.0 overview: What's new in IdentityIQ 8.0
- File attachments in access requests
- Enabling file attachments
- Required vs. optional attachments
- Adding file attachments to access requests
- Viewing attachments when approving requests
- Who can view attachments
- Working with attachment rules
- Sample attachment configuration rule - Contractor work authorization form
- The rule type
- Who this rule applies to
- Required attachments in the UI
- Attachment overlay text
- Error message - Missing attachment
File attachments in access requests
The new attachments feature enables users to add attachments to single-user access requests. For example, you could attach a training certificate or a notarized document of authorization to a request.
Here are some key points for this feature:
- The option for including attachments can be switched on or off, system-wide
- Attachments can only be used with single-identity access requests. That is, the attachment option is not available for access requests that include multiple identities.
- You can add multiple attachments to each request item
- You can add attachments to permitted roles that may be included with an access request item
- You can designate items as requiring attachment, via rules
- You can review attachments during the approval process, and when the access request is archived
- File size and type limits for attachments are configured globally
- The feature supports encryption of file attachments
- In version 8.0 of IdentityIQ, attachments are NOT supported in custom workflow/forms
Enabling file attachments
To enable the file attachments feature:
- Click the gear menu and navigate to Global Settings > IdentityIQ Configuration
- Click the Miscellaneous tab
- In the Attachment Settings section of the Miscellaneous tab, enable and configure file attachments:
- Enable Attachments: check the box to enable file attachments
- Maximum file size (MB): set the maximum file size, in megabytes, for each attachment. The default is 5 MB, and the system maximum is 20 MB.
- Supported file types: list the types of file attachments you want to support, in a comma-separated list. You do NOT need to include a dot prefix for the file type. For example, txt, jpg, png, pdf
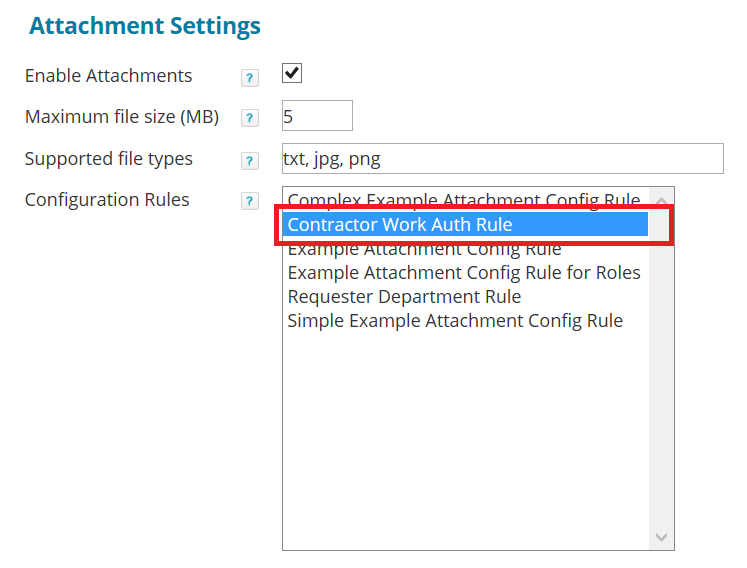
- Configuration Rules: if you want to require attachments for particular use cases (such as job title, location, et cetera), use a rule to enforce the requirement. Any Attachment Configuration rules that have been confirmed on your IdentityIQ instance are listed here. You can select multiple rules to implement, by using Ctrl-click. Note, only rules with a rule type of AttachmentConfig are used to govern attachment behavior and are listed here.
- Save your changes.
Required vs. optional attachments
When you enable attachments, you can make them either optional, or required. Requirements for attachments are managed through rules, and rule logic gives you flexibility on how to implement your requirements for attachments. For example, you might require attachments based on job title, location, the specific access being requested, et cetera. You can implement multiple rules to manage various use cases or requirements. IdentityIQ version 8.0 includes some sample rules that you can use as a model for developing your own.
Rules that govern file attachments are of rule type AttachmentConfig. Any rules with a type of AttachmentConfig appear in the selection list of rules in Global Settings. You can choose more than one rule to govern requirements for attachments; use Ctrl-click to select multiple rules to activate. Some sample rules are included out-of-the-box with IdentityIQ version 8.0.
Attachment rules are inactive by default. To activate rules that govern attachments:
- Click the gear menu and navigate to Global Settings > IdentityIQ Configuration
- Click the Miscellaneous tab.
- In the Attachment Settings section of the Miscellaneous tab, click to select all the rules you want to activate. Use Ctrl-click to select multiple rules. Selected rules are highlighted in blue.
- Save your changes. When you save your changes, the active rules remain highlighted.
Adding file attachments to access requests
When you create an Access Request, file attachments can be added on the Review and Submit tab of the request. Attachments are added to individual access request items, and can also be added for specific roles that may be included with the access request item. Note that attachments can NOT be added to requests that encompass multiple identities; they can be added for single-identity requests only.
To add an attachment, click the attachment (paper clip) icon. You can browse to files, or drag and drop them into the dialog:
Once you've added an attachment, you have the option to add a description, download the attachment, or delete the attachment. You can also add more attachments to the request.
If you try to add an attachment for a file type that is not supported, or that exceeds the maximum file size that was configured for attachments, you will see an error.
Viewing attachments when approving requests
When an Access Request item includes file attachments, the reviewer sees a green attachment icon indicating the presence and number of attachments. The reviewer can click the icon to download and view the attachment. IdentityIQ does not have any built-in viewers; in order to open and view an attachment, the user must have the appropriate application installed (for example, Adobe Acrobat or similar, to open and view a PDF attachment).
Who can view attachments
The requester or the requestee can view and download the attachment via the Access Request details. Approval owners can view or download the attachment in the approval. System Administrators can also view and download attachments at any stage of the request or review process. Other users will see that an attachment has been included, but will not be able to access the attachment for viewing or download.
Working with attachment rules
Rules that govern requirements for attachments use BeanShell to determine the rule's behavior. BeanShell provides a great deal of flexibility in what your rules can do, including things like who or what the rule applies to, and what messaging the UI will show users regarding attachments. This section shows a simple example rule, to help you understand how to create your own attachment rules.
Sample attachment configuration rule - Contractor work authorization form
This sample attachment configuration rule enforces a requirement that any time access is requested for a contractor identity, a Contractor Authorization Form must be attached to the request. The sections below explain some specific areas of the rule's elements and BeanShell code.
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE sailpoint PUBLIC "sailpoint.dtd" "sailpoint.dtd">
<sailpoint>
<Rule language="beanshell" name="Contractor Work Auth Rule" type="AttachmentConfig">
<Description>Returns configs for contractor work authorization.</Description>
<Signature returnType="java.util.List">
<Inputs>
<Argument name="log">
<Description>
</Description>
</Argument>
<Argument name="context">
<Description>
</Description>
</Argument>
<Argument name="requester" type="sailpoint.object.Identity">
<Description>
</Description>
</Argument>
<Argument name="requestee" type="sailpoint.object.Identity">
<Description>
</Description>
</Argument>
<Argument name="requestedItem" type="sailpoint.object.SailPointObject">
<Description>
</Description>
</Argument>
<Argument name="action" type="java.lang.String">
<Description>
</Description>
</Argument>
</Inputs>
<Returns>
<Argument name="configList">
<Description>
</Description>
</Argument>
</Returns>
</Signature>
<Source>
import sailpoint.object.*;
import java.util.*;
import sailpoint.service.*;
import sailpoint.tools.Util;
// Result is always a list of AttachmentConfigDTOs. The list may be empty but shouldn't be null.
List result = new ArrayList();
if (requestee != null) {
String employeeType = requestee.getType();
if (Util.nullSafeEq(employeeType, "contractor") && Util.nullSafeEq(action, "add")) {
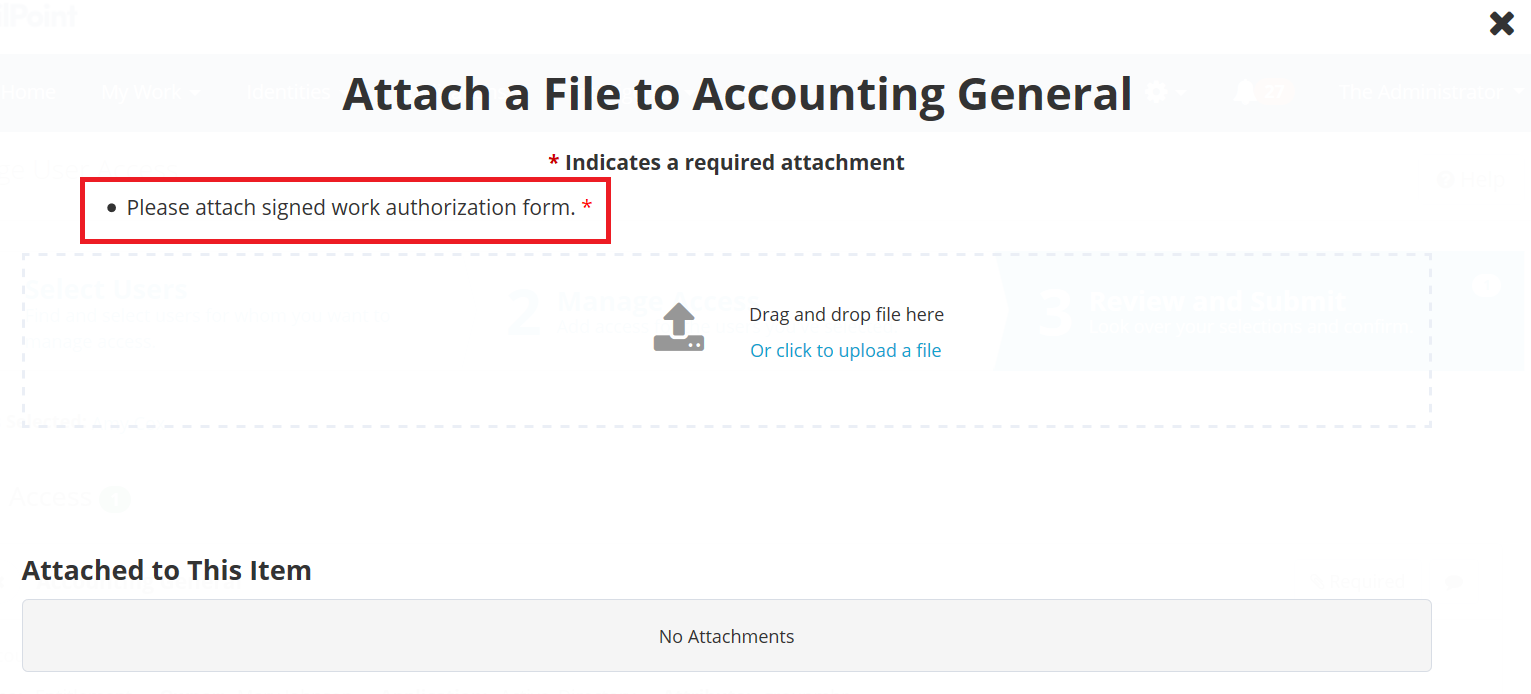
result.add(new AttachmentConfigDTO(true, "Please attach signed work authorization form."));
}
}
return result;
</Source>
</Rule>
</sailpoint>
The rule type
In the Rule element of the XML, the rule type is specified as AttachmentConfig. This is what indicates that the rule applies to Attachments, and what makes the rule appear in the Attachment Settings area of the IdentityIQ Global Configuration (gear menu > Global Settings > IdentityIQ Configuration > Miscellaneous Tab). The Rule element also provides the name of the rule as it will appear in the configuration UI.
<Rule language="beanshell" name="Contractor Work Auth Rule" type="AttachmentConfig">
Who this rule applies to
The bolded BeanShell code here specifies that this rule applies to identities of employee type "contractor":
if (requestee != null) {
String employeeType = requestee.getType();
if (Util.nullSafeEq(employeeType, "contractor")) && Util.nullSafeEq(action, "add")) {
result.add(new AttachmentConfigDTO(true, "Please attach signed work authorization form."));
Required attachments in the UI
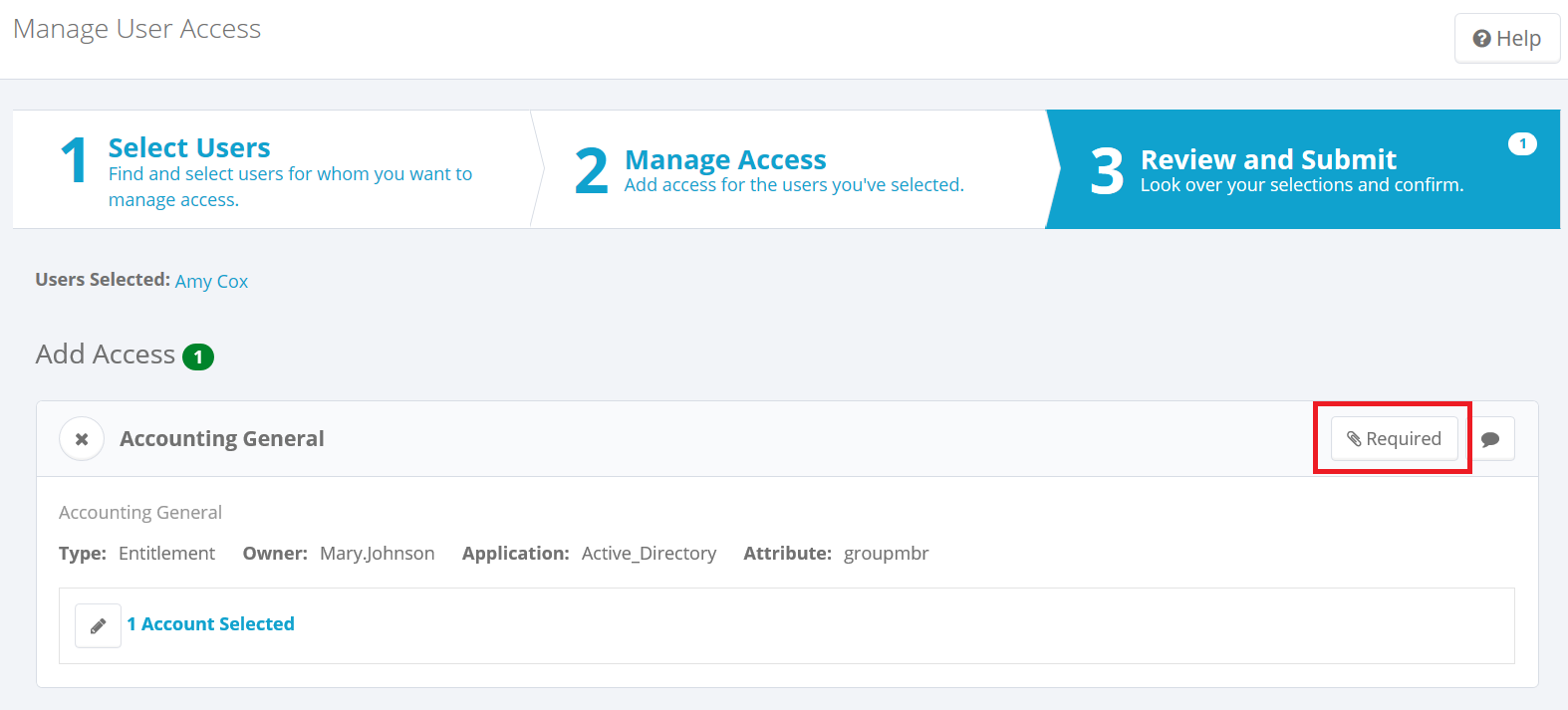
Here's an example of the Access Request UI showing a request for a user who is a contractor; with our sample Contractor Work Auth Rule in force. Note that the attachment icon includes text indicating that it is required.
Attachment overlay text
The BeanShell code can also determine the message that appears on the overlay screen when the requestor clicks the Attachment link.
if (requestee != null) {
String employeeType = requestee.getType();
if (Util.nullSafeEq(employeeType, "contractor")) && Util.nullSafeEq(action, "add")) {
result.add(new AttachmentConfigDTO(true, "Please attach signed work authorization form."));
Error message - Missing attachment
When an attachment rule is enabled, the requestor will see an error message if they try to submit an access request without the required attachment.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Nice feature, it would be good to allow requestee to attach files even after the request is submitted. An example would be that the approver is requiring further documentation
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
@cathy_mallet Where are the attachments stored? Are they stored in the DB?
Thanks.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
@GreeneT , yes, they are stored in the database (encrypted).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
@cathy_mallet Thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Nice feature. We have a requirement for uploading reference documents. it is helpful
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Can we enable this feature in 7.3 environment ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Why is it not available for access requests that include multiple identities? It could be very helpful.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
This looks great - Is there any way we can expand this feature to strip attachments from an incoming email? i.e. for a pass request system, users must submit an image which is done via email (due to security filtering etc. it remains the preferred method).
We'd like IIQ to strip the attachment automatically and attach it to a request, which will be necessary to complete birthright access provisioning. We could then use smarts around emailID etc. to link it up with the joining identity.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi,
Are there anymore examples on AttachmentConfig rules?
We want to enforce attachment requirement for specific roles, can we get requested roles from requestedItem?
Please advise
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
@cathy_mallet this is great!
I notice it is specifically mentioned that this feature is not available for custom workflows/forms in IdentityIQ 8.0 - Do you know if it is now possible to leverage this capability with custom workflows in IdentityIQ 8.1 (or targeted for a future version?) If not, can you provide point me in a direction or provide further details on how the attachment feature is implemented in OOTB access requests such that my team might be able to code a solution for to replicate this capability for a custom workflow?
Many thanks.

