- Products & services Products & services
- Resources ResourcesLearning
- Learning
- Identity University Get technical training to ensure a successful implementation
- Training paths Follow a role-based or product-based training path
- SailPoint professional certifications & credentials Advance your career or validate your identity security knowledge
- Training onboarding guide Make of the most of training with our step-by-step guide
- Training FAQs Find answers to common training questions
- Community Community
- Compass
- :
- Discuss
- :
- Community Wiki
- :
- IdentityIQ Wiki
- :
- Aggregating a single account from an application
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
Aggregating a single account from an application
Aggregating a single account from an application
- Overview
- Approaches to single account aggregation
- The user interface / LCM approach
- The application configuration approach
- The API based approach
- Execution of the API approach
- Reference artifacts
- Forum discussions related to this topic
Overview
Deployment professionals configuring IdentityIQ sometimes a need to update IdentityIQ's model of a single account from an Application without the overhead and time needed for a full re-aggregation of all accounts from the Application. This concept is called "single account aggregation", "targeted aggregation", or "single-account targeted aggregation". These terms can be use interchangeably. This article discusses approaches and examples that can be used to achieve single account aggregation in IdentityIQ.
By default, IdentityIQ aggregations process every account from the Application(s) being aggregated. This behavior is designed to support the Access Review and Certification features of IdentityIQ where a complete, current, and accurate data set is required for a Certification to be valid. When using IdentityIQ for provisioning and access-request and request-approval functions, a more real-time approach to retrieving the status of an account is necessary.
Most connector technologies in IdentityIQ support the concept of "Single account" aggregation. An notable exception to this is the delimited file connector, which due to the nature of how it reads data from a large delimited file, is unable to retrieve a single individual account. In addition, the JDBC connector requires the "getObjectSQL" parameter to be configured to support retrieving Account information one account at a time. For most other connectors, the capability to retrieve an account in a one-off fashion is built into the connector technology. At the code layer of the connector technology, the connector class must support the "getObject()" method in order to support single-account aggregation.
Approaches to single account aggregation
There are three ways in IdentityIQ to update the model of a single account, without running a full account aggregation against an application:
1) Via the user interface for LCM under Manage Access -> Manage Accounts -> For Others, select the Identity correlated to the account.
2) Modify the Application configuration temporarily with a filter include only the desired accounts, then run an aggregation.
3) Programmatically via the API, invoke the Aggregator to aggregate the single account directly.
The user interface / LCM approach
The first option uses the LCM features of IdentityIQ to refresh the status of an Identity's accounts. Under Manage Access -> Manage Accounts -> For Others, select the Identity correlated to the account you want to re-aggregate. Most directly-connected Applications will automatically re-aggregate the account in real time to update the status of the account when this page is loaded. For other connector technologies a "refresh" button is provided on the right side of the screen which will cause IdentityIQ to re-aggregate that single specific account. An example of this part of the user interface is shown here:
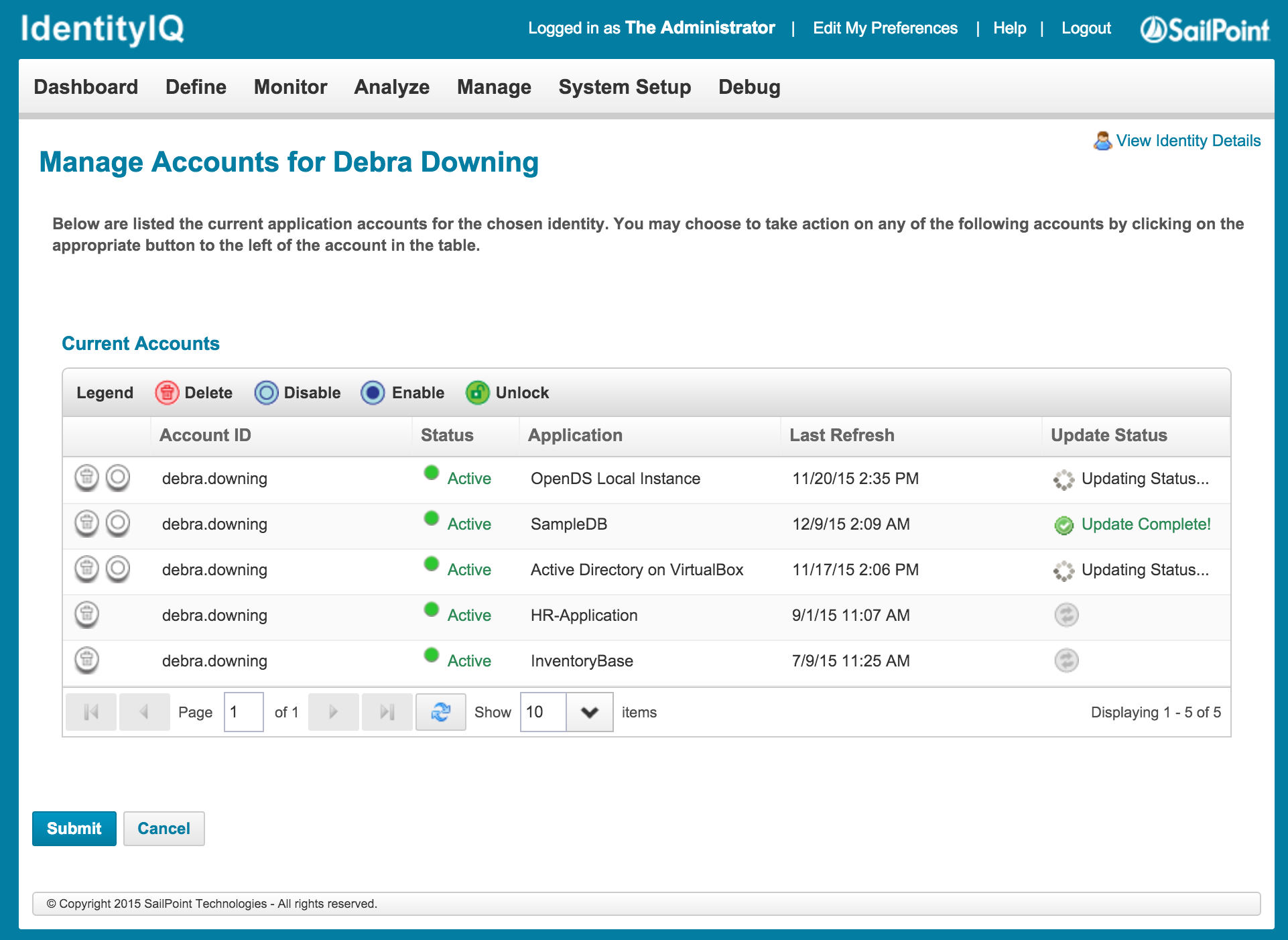
The application configuration approach
The second option, discussed here (https://community.sailpoint.com/message/10188#10188) is cumbersome in that it requires administrative access to change the Application's configuration and then the execution of a specifically configured Account Aggregation task to operate. In some scenarios it can work but in general it is not a recommended solution for everyday use.
The API based approach
The third option, the API-based option, is used to automate a number of processes on installations that need close to real-time accuracy of account information in IdentityIQ. This is the recommended approach for installations that need to electronically automate the process of having IdentityIQ update a single account's status from an Application. This approach has the advantage of allowing the user to pass information about an account that IdentityIQ has never seen before, allowing a single new account to be added to IdentityIQ's model without requiring a full re-aggregation. This approach also allows IdentityIQ to detect account deletions if the account name passed to the single account aggregation has been removed from the Application.
The following example snippet shows how to use the API-based approach, and a code review is provided below.
import sailpoint.object.Application;
import sailpoint.object.Attributes;
import sailpoint.object.Custom;
import sailpoint.object.Filter;
import sailpoint.object.Identity;
import sailpoint.object.Link;
import sailpoint.object.QueryOptions;
import sailpoint.object.ResourceObject;
import sailpoint.object.TaskResult;
import sailpoint.object.Rule;
import sailpoint.connector.JDBCConnector;
import sailpoint.api.Aggregator;
import sailpoint.connector.Connector;
import org.apache.log4j.Logger;
import org.apache.log4j.Level;
// Declare a logger class for us to isolate these messages during aggregation.
// Force the log level to DEBUG for initial testing.
Logger log = Logger.getLogger("sailpoint.services.DemonstrateSingleAccountAggregation");
log.setLevel(Level.DEBUG); // TODO: Turn this off or remove this line when checking in.
// Initialize the error message to nothing.
String errorMessage = "";
// We need some values defined to know which account we want to aggregate.
String applicationName = "SampleDB";
String accountName = "clyde.orangous";
// We have already validated all of the arguments. No just load the objects.
Application appObject = context.getObjectByName(Application.class, applicationName);
String appConnName = appObject.getConnector();
log.debug("Application " + applicationName + " uses connector " + appConnName);
Connector appConnector = sailpoint.connector.ConnectorFactory.getConnector(appObject, null);
if (null == appConnector) {
errorMessage = "Failed to construct an instance of connector [" + appConnName + "]";
return errorMessage;
}
log.debug("Connector instantiated, calling getObject() to read account details...");
ResourceObject rObj = null;
try {
rObj = (ResourceObject) appConnector.getObject("account", accountName, null);
} catch (sailpoint.connector.ObjectNotFoundException onfe) {
errorMessage = "Connector could not find account: [" + accountName + "]";
errorMessage += " in application [" + applicationName + "]";
log.error(errorMessage);
log.error(onfe);
return errorMessage;
}
if (null == rObj) {
errorMessage = "ERROR: Could not get ResourceObject for account: " + accountName;
log.eror(errorMessage);
return errorMessage;
}
log.debug("Got raw resourceObject: " + rObj.toXml());
// Now we have a raw ResourceObject. The Application in IdentityIQ may have a
// Customization rule defined to transform the ResourceObject. We need to
// honor that configuration, so if the Applicaiton has a Rule then we run it.
Rule customizationRule = appObject.getCustomizationRule();
if (null != customizationRule) {
log.debug("Customization rule found for applicaiton " + applicationName);
try {
// Pass the mandatory arguments to the Customization rule for the app.
HashMap ruleArgs = new HashMap();
ruleArgs.put("context", context);
ruleArgs.put("log", log);
ruleArgs.put("object", rObj);
ruleArgs.put("application", appObject);
ruleArgs.put("connector", appConnector);
ruleArgs.put("state", new HashMap());
// Call the customization rule just like a normal aggregation would.
ResourceObject newRObj = context.runRule(customizationRule, ruleArgs, null);
// Make sure we got a valid resourceObject back from the rule.
if (null != newRObj) {
rObj = newRObj;
log.debug("Got post-customization resourceObject: " + rObj.toXml());
}
} catch (Exception ex) {
// Swallow any customization rule errors, the show must go on!
log.error("Error while running Customization rule for " + applicationName);
}
}
// Next we perform a miniature "Aggregation" using IIQ's built in Aggregator.
// Create an arguments map for the aggregation task.
// To change this (if you need to), the map contains aggregation options and is the same as the
// arguments to the acocunt aggregation tasks. Some suggestied defaults are:
Attributes argMap = new Attributes();
argMap.put("promoteAttributes", "true");
argMap.put("correlateEntitlements", "true");
argMap.put("noOptimizeReaggregation", "true"); // Note: Set to false to disable re-correlation.
// Consturct an aggregator instance.
Aggregator agg = new Aggregator(context, argMap);
if (null == agg) {
errorMessage = "Null Aggregator returned from constructor. Unable to Aggregate!";
log.eror(errorMessage);
return errorMessage;
}
// Invoke the aggregation task by calling the aggregate() method.
// Note: the aggregate() call may take serveral seconds to complete.
log.debug("Calling aggregate() method... ");
TaskResult taskResult = agg.aggregate(appObject, rObj);
log.debug("aggregation complete.");
if (null == taskResult) {
errorMessage = "ERROR: Null taskResult returned from aggregate() call.";
log.eror(errorMessage);
return errorMessage;
}
// Show the task result details for engineers curious about the results.
// These ususally look like the following:
// <?xml version='1.0' encoding='UTF-8'?>
// <!DOCTYPE TaskResult PUBLIC "sailpoint.dtd" "sailpoint.dtd">
// <TaskResult>
// <Attributes>
// <Map>
// <entry key="applications" value="1"/>
// <entry key="exceptionChanges" value="1"/>
// <entry key="extendedAttributesRefreshed" value="1"/>
// <entry key="identityEntitlementsCreated" value="1"/>
// <entry key="identityEntitlementsIndirectLinkUpdates" value="1"/>
// <entry key="identityEntitlementsRoleAssignmentsUpdates" value="4"/>
// <entry key="identityEntitlementsRoleDetectionsUpdates" value="1"/>
// <entry key="identityEntitlementsUpdated" value="1"/>
// <entry key="total" value="1"/>
// <entry key="updated" value="1"/>
// </Map>
// </Attributes>
// </TaskResult>
// Where the "udpated" indiciates the number of account links updated.
log.debug("TaskResult details: \n" + taskResult.toXml());
return ("Success");
Lines 1 through 20 define the includes and logging.
Line 21 should be removed when using this code in production; it sets logging levels for demonstration purposes.
Lines 26 through 28 specify the Application Name and Account Name for the account to aggregate.
Lines 30 through 41 instantiate the Application and its Connector in local memory.
Lines 43 through 62 read back the "ResourceObject" from the Connector. The ResourceObject represents the account before it has been correlated and "Link"-ed to an Identity object.
Lines 64 through 99 execute the Application's Customization Rule on the ResourceObject returned from the Connector. This allows single-account aggregations to have the same customizations applied as full aggregations run from Aggregation tasks.
Lines 101 through 128 construct an instance of the Aggregator class to aggregate the single account. They return a TaskResult reference with statistics about the aggregation.
Lines 130 through 152 log the details of the Aggregation's TaskResult to the log file.
Execution of the API approach
When imported and executed from "iiq console" the code above provides the following output:
> import "/Users/adam.hampton/Documents/workspace/ssb-keppler-baremetal/config/Rule/Rule-Demonstrate-Single-Account-Aggregation.xml
Rule:Demomstrate Single Account Aggregation
> rule "Demomstrate Single Account Aggregation"
2015-12-09 10:39:37,845 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Application SampleDB uses connector sailpoint.connector.JDBCConnector
2015-12-09 10:39:37,857 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Connector instantiated, calling getObject() to read account details...
2015-12-09 10:39:37,858 DEBUG main sailpoint.connector.JDBCConnector:1048 - SQL statement[select * from users where login = 'clyde.orangous'].
2015-12-09 10:39:37,858 DEBUG main sailpoint.connector.JDBCConnector:1412 - Returned from execute [true].
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [login]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [description]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [first]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [last]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [role]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [status]
2015-12-09 10:39:37,860 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [locked]
2015-12-09 10:39:37,861 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [email]
2015-12-09 10:39:37,861 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [roleFlag]
2015-12-09 10:39:37,861 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [password]
2015-12-09 10:39:37,861 DEBUG main sailpoint.connector.JDBCConnector:1627 - Building attribute [postalcode]
2015-12-09 10:39:37,861 DEBUG main sailpoint.connector.JDBCConnector:516 - SQL statement for Direct Permission is null
2015-12-09 10:39:37,863 DEBUG main sailpoint.services.bshdemo.customizationRule:? - account [clyde.orangous] has status [A], setting disabled false.
2015-12-09 10:39:37,864 DEBUG main sailpoint.services.bshdemo.customizationRule:? - account [clyde.orangous] has locked [N], setting locked false.
2015-12-09 10:39:37,864 DEBUG main sailpoint.services.bshdemo.customizationRule:? - Performing one-time load of 'postalCodeLookupMap'...
2015-12-09 10:39:37,865 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:10007 to state:NY
2015-12-09 10:39:37,866 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:77077 to state:TX
2015-12-09 10:39:37,866 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78747 to state:TX
2015-12-09 10:39:37,866 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78748 to state:TX
2015-12-09 10:39:37,866 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78749 to state:TX
2015-12-09 10:39:37,869 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:81003 to state:CO
2015-12-09 10:39:37,869 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:90405 to state:CA
2015-12-09 10:39:37,870 DEBUG main sailpoint.services.bshdemo.customizationRule:? - No 'postalcode' field/property found on account:clyde.orangous
2015-12-09 10:39:37,871 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Got raw resourceObject: <?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE ResourceObject PUBLIC "sailpoint.dtd" "sailpoint.dtd">
<ResourceObject displayName="clyde.orangous" identity="clyde.orangous" objectType="account">
<Attributes>
<Map>
<entry key="IIQDisabled">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="IIQLocked">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="email" value="clyde.orangous@acme.com"/>
<entry key="first" value="ornage"/>
<entry key="last" value="Clyde-primus"/>
<entry key="locked" value="N"/>
<entry key="login" value="clyde.orangous"/>
<entry key="role">
<value>
<List>
<String>User</String>
</List>
</value>
</entry>
<entry key="status" value="A"/>
</Map>
</Attributes>
</ResourceObject>
2015-12-09 10:39:37,871 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Customization rule found for applicaiton SampleDB
2015-12-09 10:39:37,873 DEBUG main sailpoint.services.bshdemo.customizationRule:? - account [clyde.orangous] has status [A], setting disabled false.
2015-12-09 10:39:37,874 DEBUG main sailpoint.services.bshdemo.customizationRule:? - account [clyde.orangous] has locked [N], setting locked false.
2015-12-09 10:39:37,874 DEBUG main sailpoint.services.bshdemo.customizationRule:? - Performing one-time load of 'postalCodeLookupMap'...
2015-12-09 10:39:37,875 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:10007 to state:NY
2015-12-09 10:39:37,875 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:77077 to state:TX
2015-12-09 10:39:37,875 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78747 to state:TX
2015-12-09 10:39:37,876 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78748 to state:TX
2015-12-09 10:39:37,876 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:78749 to state:TX
2015-12-09 10:39:37,876 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:81003 to state:CO
2015-12-09 10:39:37,876 DEBUG main sailpoint.services.bshdemo.customizationRule:? - loaded mapping of zipcode:90405 to state:CA
2015-12-09 10:39:37,877 DEBUG main sailpoint.services.bshdemo.customizationRule:? - No 'postalcode' field/property found on account:clyde.orangous
2015-12-09 10:39:37,878 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Got post-customization resourceObject: <?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE ResourceObject PUBLIC "sailpoint.dtd" "sailpoint.dtd">
<ResourceObject displayName="clyde.orangous" identity="clyde.orangous" objectType="account">
<Attributes>
<Map>
<entry key="IIQDisabled">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="IIQLocked">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="email" value="clyde.orangous@acme.com"/>
<entry key="first" value="ornage"/>
<entry key="last" value="Clyde-primus"/>
<entry key="locked" value="N"/>
<entry key="login" value="clyde.orangous"/>
<entry key="role">
<value>
<List>
<String>User</String>
</List>
</value>
</entry>
<entry key="status" value="A"/>
</Map>
</Attributes>
</ResourceObject>
2015-12-09 10:39:37,878 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - Calling aggregate() method...
2015-12-09 10:39:39,010 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - aggregation complete.
2015-12-09 10:39:39,011 DEBUG main sailpoint.services.DemonstrateSingleAccountAggregation:? - TaskResult details:
<?xml version='1.0' encoding='UTF-8'?>
<!DOCTYPE TaskResult PUBLIC "sailpoint.dtd" "sailpoint.dtd">
<TaskResult>
<Attributes>
<Map>
<entry key="applications" value="SampleDB"/>
<entry key="identityEntitlementsIndirectLinkUpdates" value="1"/>
<entry key="identityEntitlementsIndirectUpdates" value="1"/>
<entry key="identityEntitlementsRoleAssignmentsUpdates" value="1"/>
<entry key="identityEntitlementsRoleDetectionsUpdates" value="1"/>
<entry key="identityEntitlementsUpdated" value="1"/>
<entry key="internalUpdates" value="1"/>
<entry key="total" value="1"/>
<entry key="updated" value="1"/>
</Map>
</Attributes>
</TaskResult>
Success
Reference artifacts
Two examples are attached to this document: A Workflow, and a Rule that implements the API-based approach for reference. These can be used as copy/paste ready examples for use in your projects.
Forum discussions related to this topic
The following list includes older forum discussions related to this topic that may have partially correct or outdated information related to this topic.
- https://community.sailpoint.com/message/11408#11408
- https://community.sailpoint.com/message/10300#10300
- https://community.sailpoint.com/message/12344#12344
- https://community.sailpoint.com/message/11378#11378
- https://community.sailpoint.com/message/30750#30750
- https://community.sailpoint.com/message/14535#14535
- https://community.sailpoint.com/message/10188#10188
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
6.1... yeah. You don't even have partitioning support in that edition. The AD connector there is missing loads and loads of features that later releases have. Do you have your JVM's configured to close the AD connections after a timeout? It's kind-of grasping at straws, but one other thing that might help improve stability:
--Adam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Thanks Adam, I'll pass that on to the app server team so they can verify. I'm hoping they can find something. What's really odd is that we've been pretty stable until about a few weeks ago. We haven't yet been able to pinpoint any kind of change that might be root cause, but if we find anything interesting I'll post it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Adam, quick update. So all the aggregations ran fine in ALL regions last night (not just where I was trying out the changes you suggested). Our network and AD guys found some "obsolete IPs returned in the DNS queries for the domaindnszones lookups". We're not sure if this is root cause just yet, but we'll be monitoring over the next week or two to see if thing stablize.
Do the 6.4 and 7.x versions have any enhancements that allow IIQ to gracefully deal with DNS and a "down" server/situation?
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Glad to hear the aggregations ran fine! Yes and no, there aren't any specific features for dealing with an offline DC host more gracefully. 6.4 and 7.0 do allow you to hard-code a list of IP Addresses for the servers to communicate to on the LDAP side. If the first in the list is offline then IdentityIQ can try the second, and so on. This might have helped your situation, assuming the IPs in IdentityIQ were not ones that became obsolete.
If DNS or "round-robin" DNS or "local-DC-host-preferred" DNS resolves to an IP for a host that is offline then there is little to nothing IdentityIQ can do to work around the issue. IdentityIQ doesn't maintain its own internal list of DC hosts in a domain and the set of DC hosts can change from day-to-day. Maintaining DNS lists with respect to which DC hosts are online and available can be a challenge for sure. IdentityIQ relies on DNS on it's LDAP side and .net bindings on the IQService side to return a host-name/IP for a DC host that is online and available. I'd be surprised if your AD team wasn't dealing with other issues related to AD if they had invalid IP addresses in a round-robin DNS or ordered bind list.
This could simply be a case of "Garbage in, garbage out", where a SNAFU in an up-stream system setup (in this case DNS) caused IdentityIQ issues.
Cheers,
--Adam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
I've tried running this code after disabling and moving a user in Active Directory. However, the link remains with partial data (the only remaining attribute is IIQDisabled and the link is listed as disabled="true"). Do you know how to fully delete the link from the identity in this case?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi Sean,
I am have a similar issue with my aggregation rule:
The application script threw an exception: sailpoint.connector.AuthenticationFailedException: Failed to connect to server:Required String attribute : authorizationType value was null.
My IIQ version is 7.0. When I am adding the authorization type at root, it is giving below exception :
Exception running rule: The application script threw an exception: sailpoint.connector.AuthenticationFailedException: Failed to connect to server:Required String attribute : host value was null. It must have a valid value. BSF info
I have multiple domains in my case, also the existing Application XML has no tag as <host>. The domain settings section is given below :
<entry key="domainSettings">
<value>
<List>
<Map>
<entry key="authorizationType" value="simple"/>
<entry key="domainDN" value="DC=test,DC=Corp,DC=test"/>
<entry key="password" value="1:LxxAYB+m"/>
<entry key="port" value="389"/>
<entry key="servers">
<value>
<List>
<String>10.xx.xx.xx1</String>
</List>
</value>
</entry>
<entry key="useSSL">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="user" value="saidm"/>
</Map>
<Map>
<entry key="authorizationType" value="simple"/>
<entry key="domainDN" value="DC=test2,DC=Corp,DC=test"/>
<entry key="password" value="1:LxxAYB+m"/>
<entry key="port" value="389"/>
<entry key="servers">
<value>
<List>
<String>10.xx.xx.xx</String>
</List>
</value>
</entry>
<entry key="useSSL">
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key="user" value="saidm"/>
</Map>
</List>
</value>
</entry>
Can you help?
Regards,
Debapriya
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
I'm pretty certain at least one "host" entry is required for an Active Directory application. There are parts of IdentityIQ's AD connector code that require a domain controller host name of "last resort" to connect to. Not all operations use server-less binding; specifically the Java + LDAP side of the connector require a target host name.
--Adam
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi Sean,
I'm using a single-account targeted AD aggregation with 7.0p1 and I'm getting some weird behaviour.
I'm not receiving the error you have indicated, but my ResourceObjects are being imported without memberOf values.
I'm wondering if this could be related to the same issue - have you noticed any such behaviour?
- Ryan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi Adam,
I'm using a single-account targeted AD aggregation with 7.0p1 and my ResourceObjects are being imported without memberOf values. This does not occur when performing a full aggregation.
For testing purposes:
1/ I've increased the sailpoint.connector logging to TRACE level
2/ I've created an application with an LDAP filter that only includes a single account
3/ I've performing a full aggregation and a targeted aggregation against that account in the application.
4/ Logging indicates that the memberOf values are being retrieved from AD for both full and targeted aggregation
5/ However, groups are only discovered succesfully for the full aggregation
I suspect this is a product bug.
Since I can't attach files to this comment, here are the relevant sections of the trace for each. If you compare these in a suitable text comparison product, you will find that there are significant differences beginning at the following line (full aggregation has a ContainerIterator, targeted does not):
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:122 - Entering getGroupMembershipSearchDN()
1/ Full aggregation
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting buildAttributes = {displayName=GGGG,KZZ, employmentAUIntPreferredSurname=GGGG, description=Group1, distinguishedName=CN=KG9999,OU=Users,DC=contoso,DC=local, title=Just Some Guy, employeeNumber=99999999, postOfficeBox=GPO Box 9880, objectguid={005c7753-6b14-4aca-81eb-48f3fa217480}, sn=GGGG, memberOf=[CN=Group1,OU=Groups,DC=contoso,DC=local, CN=Group2,OU=Resource,OU=Groups,DC=contoso,DC=local], department=Education Departmental, info=Created by IdentityIQ on 2016-06-30, extensionAttribute2=SSC, sAMAccountName=KG9999, extensionAttribute1=Org.Dept.SSC, initials=KG, givenName=KZZ, extensionAttribute3=Addressees, objectClass=[top, person, organizationalPerson, user], cn=KG9999, employeeType=Ongoing FT, postalAddress=GPO Box 9880, CANBERRA ACT 2601, primaryGroupID=513, objectSid=S-1-5-21-2836116808-2396222863-416691703-495342, msDS-PrincipalName=CONTOSO\KG9999}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1912 - display attribute:sAMAccountName value:KG9999
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1920 - Server type is AD.Retrieving group membership value from groups
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipAttribute(membershipAttribute = posixGroup_Member_Attribute)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:5530 - config attribute for membership:posixGroup_Member_Attribute
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = enablePosixGroups)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:5545 - Feature against config attribute posixGroup_Member_Attribute has not been enabled.
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@10d49e70[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2021 - Definition of nisnetgroups not specified .Skipping netgroup memberships for user:CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDNs()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDn()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDn = [Ljava.lang.String;@62b02dd1
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDNs = [Ljava.lang.String;@62b02dd1
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering escapeLDAPSearchFilter(strFilter = CN=KG9999,OU=Users,DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting escapeLDAPSearchFilter = CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member, customFilter = null)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberFilterString)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getDefaultGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getDefaultGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembership(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, searchString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local)))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2575 - Within getGroupMembership()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2585 - Retrieved group schema
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering isDomainSettingDefined()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = domainSettings)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = *****
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting isDomainSettingDefined = true
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getMembershipConnectionForDomainSetting()
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createDomainCtxMapFromDomainSetting(bRemoveSpaces = true, domainList = null)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getCommonConnectionSetting()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useSSL)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5013 - Incorporating facility to retrieve objectGUID
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = ldapContextFactory)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = referral)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = ignore
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering isConnectionPoolingDisabled()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = disablePooling)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting isConnectionPoolingDisabled = false
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttributes()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttributes = {authSearchAttributes=[sAMAccountName], acctAggregationEnd=Wed Jul 06 16:27:02 AEST 2016, deltaIterationMode=DEFAULT, nativeChangeDetectionAttributeScope=entitlements, IQServicePort=5050, acctAggregationStart=Wed Jul 06 16:27:02 AEST 2016, pageSize=500, manageRecycleBin=false, nativeChangeDetectionOperations=null, compositeDefinition=null, forestAdmin=null, group.searchDNs=[{searchDN=OU=Groups,DC=contoso,DC=local, searchScope=SUBTREE, iterateSearchFilter=objectclass=Group}], forestGC=null, manageLync=true, sysDescriptions={en_US=null}, nativeChangeDetectionEnabled=false, domainSettings=*****, deletedObjectsContainer=CN=Deleted Objects,DOMAIN, useSSL=false, IQServiceHost=EDEISEC026, templateApplication=Active Directory Template, referral=ignore, nativeChangeDetectionAttributes=null, forestAdminPassword=*****, exchangeversion=2013, lyncAttributes=RegistrarPool,SipAddressType,SipAddress,SipDomain,msRTCSIP-UserEnabled, searchDNs=[{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]}
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getCommonConnectionSetting = {java.naming.referral=ignore, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid}
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = domainSettings)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = *****
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5410 - Going to create the context for domain DN : DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createContextForDomainConfig(domainSetting = {password=*****, servers=[DC1.contoso.local], port=389, authorizationType=simple, user=Service_IQAdmin_d, domainDN=DC=contoso,DC=local, useSSL=false}, env = {java.naming.referral=ignore, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid})
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5118 - Going to create the context for domain DN : DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = useServerless)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createContext(env = {java.naming.referral=ignore, java.naming.security.principal=Service_IQAdmin_d, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid, java.naming.provider.url=ldap://DC1.contoso.local:389, java.naming.security.credentials=*****, java.naming.security.authentication=simple})
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5445 - Connected server with url:ldap://DC1.contoso.local:389
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createContext = javax.naming.ldap.InitialLdapContext@313163a4
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering validateLDAPContext(ctx = javax.naming.ldap.InitialLdapContext@313163a4, domainDN = DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5288 - Entering validateLDAPContext
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5300 - LDAP Search successful, context validated!!!
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5307 - Exiting validateLDAPContext
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting validateLDAPContext = true
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createContextForDomainConfig = javax.naming.ldap.InitialLdapContext@313163a4
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createDomainCtxMapFromDomainSetting = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@313163a4}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getMembershipConnectionForDomainSetting = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@313163a4}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getSearchControls(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1209 - Within getSearchControls()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>], name = searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>], name = searchScope, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = group.searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupsearchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getIntAttribute(name = searchCountLimit)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getIntAttribute = 0
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getIntAttribute(name = searchTimeLimit)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getIntAttribute = 0
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = searchReturningObj)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = searchDeferLink)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getSearchControls(objectType = group, options = null, scope = null, countLimit = 0, timeLimit = 0, returningObj = false, deferLink = false)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering resolveScope(scope = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting resolveScope = 2
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getAttrNames(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1624 - Within getAttrNames()
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getAttributesToRetrieve(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getAttributesToRetrieve(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemaAttributeNames(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@c63c9de[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemaAttributeNames = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getAttributesToRetrieve = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy]
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getAttributesToRetrieve = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy, userAccountControl, msds-user-account-control-computed]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = revokeAttr)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1632 - Cannot fetch revoke information of user as no revoke attribute has been specified
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = lockAttr)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1645 - Cannot fetch locked information of user as no lock attribute has been specified
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1714 - Exitting getAttrNames()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getAttrNames = [Ljava.lang.String;@115cecae
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getSearchControls = javax.naming.directory.SearchControls@1210fdb2
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1222 - Retrieved search control for group;scope:null;countLimit=0;timeLimit:0;deferlink=false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1227 - Exitting getSearchControls()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getSearchControls = javax.naming.directory.SearchControls@1210fdb2
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@10d49e70[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@10d49e70[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@10d49e70[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2606 - Group membership attribute:member
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberSearchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:122 - Entering getGroupMembershipSearchDN()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:128 - Exiting getGroupMembershipSearchDN = [Ljava.lang.String;@71ad8484
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:122 - Entering getGroupMembershipSearchDN()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:128 - Exiting getGroupMembershipSearchDN = [Ljava.lang.String;@71ad8484
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2644 - Search string:(&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2650 - Searching in base:OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2651 - Search: (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local)) dn: OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getContextForDN(domainContextMap = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@313163a4}, searchDN = OU=Groups,DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = OU=Groups,DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = ou=general,ou=groups,ou=department,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering lookupDNFromDomainCtxMap(domainContextMap = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@313163a4}, searchDN = ou=general,ou=groups,ou=department,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = ou=general,ou=groups,ou=department,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = ou=general,ou=groups,ou=department,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting lookupDNFromDomainCtxMap = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5471 - Unable to created LdapContext from DomainSettings
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getContextForDN = javax.naming.ldap.InitialLdapContext@313163a4
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2656 - Getting the context from _domainContextMap
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getCompositeName(baseDN = OU=Groups,DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getCompositeName = OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2792 - Completed search
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@4bbbe556)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = true
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2799 - Found group:CN=Group2,OU=Resource,OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@4bbbe556)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = true
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2799 - Found group:CN=Group1,OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@4bbbe556)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2815 - Exitting getGroupMembership()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembership = [CN=Group2,OU=Resource,OU=Groups,DC=contoso,DC=local, CN=Group1,OU=Groups,DC=contoso,DC=local]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2092 - Setting ResourceObject Uuid :{005c7753-6b14-4aca-81eb-48f3fa217480}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2105 - Created resource object for identity:CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2110 - Exitting buildObject()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting buildObject = sailpoint.object.ResourceObject@3d744913
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering primaryGroupLookup(schema = sailpoint.object.Schema@38f0e7ae[id=8a8b80b3555b69f40155bde293db6845,name=<null>])
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting primaryGroupLookup = true
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteArray(SID = S-1-5-21-2836116808-2396222863-416691703-495342)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@281cce62
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 21)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@3588e641
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2836116808)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@218d24f3
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2396222863)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@3eaedd00
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 416691703)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@700f7b69
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 495342)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@2c721c7
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteArray = [B@4aa537d0
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering lookupPrimaryGroup(context = com.sun.jndi.ldap.LdapCtx@22bb559, primaryGroupId = 513, userSid = [B@4aa537d0)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering buildPrimaryGroupSID(userSid = [B@4aa537d0, primaryGroupId = 513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@4aa537d0)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-495342
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2719 - USERS-SID: S-1-5-21-2836116808-2396222863-416691703-495342
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@9f45246)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-0
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2728 - CHOPPED-SID: S-1-5-21-2836116808-2396222863-416691703-0
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2735 - REBUILT: S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting buildPrimaryGroupSID = S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteArray(SID = S-1-5-21-2836116808-2396222863-416691703-513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@320683a6
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 21)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@51fe2981
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2836116808)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@e20cf9a
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2396222863)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@25edda7a
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 416691703)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@23f076d2
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@362e10c
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteArray = [B@bb6a2e5
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@bb6a2e5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2277 - REBUILT-GROUP-SID: S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering resolveDN(ctx = com.sun.jndi.ldap.LdapCtx@22bb559, SIDBytes = [B@bb6a2e5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteString(sid = [B@bb6a2e5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteString = \01\05\00\00\00\00\00\05\15\00\00\00\48\b5\0b\a9\8f\75\d3\8e\f7\35\d6\18\01\02\00\00
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getPrimarySearchDN()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:122 - Entering getPrimaryGroupSearchDn()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector$ContainerIterator:128 - Exiting getPrimaryGroupSearchDn = OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getPrimarySearchDN = OU=Groups,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@40c387e3)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = false
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting resolveDN = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2282 - GROUPDN: null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting lookupPrimaryGroup = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:1011 - unable to resolve PrimaryGroupDn for obj:CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering resolveAccountStates(obj = sailpoint.object.ResourceObject@3d744913, controlFlags = 512, computedControlFlags = 0)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getUserAccessControlMap()
2/ Targeted aggregation
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting buildAttributes = {displayName=GGGG,KZZ, employmentAUIntPreferredSurname=GGGG, description=Group1, distinguishedName=CN=KG9999,OU=Users,DC=contoso,DC=local, title=Just Some Guy, employeeNumber=99999999, postOfficeBox=GPO Box 9880, objectguid={005c7753-6b14-4aca-81eb-48f3fa217480}, sn=GGGG, memberOf=[CN=Group1,OU=Groups,DC=contoso,DC=local, CN=Group2,OU=Resource,OU=Groups,DC=contoso,DC=local], department=Education Departmental, info=Created by IdentityIQ on 2016-06-30, extensionAttribute2=SSC, sAMAccountName=KG9999, extensionAttribute1=Org.Dept.SSC, initials=KG, givenName=KZZ, extensionAttribute3=Addressees, objectClass=[top, person, organizationalPerson, user], cn=KG9999, employeeType=Ongoing FT, postalAddress=GPO Box 9880, CANBERRA ACT 2601, primaryGroupID=513, objectSid=S-1-5-21-2836116808-2396222863-416691703-495342, msDS-PrincipalName=CONTOSO\KG9999}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1912 - display attribute:sAMAccountName value:KG9999
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1920 - Server type is AD.Retrieving group membership value from groups
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipAttribute(membershipAttribute = posixGroup_Member_Attribute)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:5530 - config attribute for membership:posixGroup_Member_Attribute
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = enablePosixGroups)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:5545 - Feature against config attribute posixGroup_Member_Attribute has not been enabled.
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@663b8efa[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2021 - Definition of nisnetgroups not specified .Skipping netgroup memberships for user:CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDNs()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDn()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDn = [Ljava.lang.String;@42a19f8e
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDNs = [Ljava.lang.String;@42a19f8e
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering escapeLDAPSearchFilter(strFilter = CN=KG9999,OU=Users,DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting escapeLDAPSearchFilter = CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member, customFilter = null)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberFilterString)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getDefaultGroupMembershipFilterString(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, objectClass = Group, memberAttribute = member)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getDefaultGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipFilterString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembership(identity = CN=KG9999,OU=Users,DC=contoso,DC=local, searchString = (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local)))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2575 - Within getGroupMembership()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2585 - Retrieved group schema
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering isDomainSettingDefined()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = domainSettings)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = *****
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting isDomainSettingDefined = true
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getMembershipConnectionForDomainSetting()
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createDomainCtxMapFromDomainSetting(bRemoveSpaces = true, domainList = null)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getCommonConnectionSetting()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useSSL)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5013 - Incorporating facility to retrieve objectGUID
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = ldapContextFactory)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = referral)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = ignore
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering isConnectionPoolingDisabled()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = disablePooling)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting isConnectionPoolingDisabled = false
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttributes()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttributes = {authSearchAttributes=[sAMAccountName], acctAggregationEnd=Wed Jul 06 13:03:11 AEST 2016, deltaIterationMode=DEFAULT, nativeChangeDetectionAttributeScope=entitlements, IQServicePort=5050, acctAggregationStart=Wed Jul 06 13:03:11 AEST 2016, pageSize=500, manageRecycleBin=false, nativeChangeDetectionOperations=null, compositeDefinition=null, forestAdmin=null, group.searchDNs=[{searchDN=OU=Groups,DC=contoso,DC=local, searchScope=SUBTREE, iterateSearchFilter=objectclass=Group}], forestGC=null, manageLync=true, sysDescriptions={en_US=null}, nativeChangeDetectionEnabled=false, domainSettings=*****, deletedObjectsContainer=CN=Deleted Objects,DOMAIN, useSSL=false, IQServiceHost=EDEISEC026, templateApplication=Active Directory Template, referral=ignore, nativeChangeDetectionAttributes=null, forestAdminPassword=*****, exchangeversion=2013, lyncAttributes=RegistrarPool,SipAddressType,SipAddress,SipDomain,msRTCSIP-UserEnabled, searchDNs=[{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]}
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getCommonConnectionSetting = {java.naming.referral=ignore, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid}
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = domainSettings)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = *****
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5410 - Going to create the context for domain DN : DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createContextForDomainConfig(domainSetting = {password=*****, servers=[DC1.contoso.local], port=389, authorizationType=simple, user=Service_IQAdmin_d, domainDN=DC=contoso,DC=local, useSSL=false}, env = {java.naming.referral=ignore, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid})
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5118 - Going to create the context for domain DN : DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = useServerless)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering createContext(env = {java.naming.referral=ignore, java.naming.security.principal=Service_IQAdmin_d, java.naming.factory.initial=com.sun.jndi.ldap.LdapCtxFactory, com.sun.jndi.ldap.connect.pool=true, java.naming.ldap.attributes.binary=objectguid objectSid msExchMailboxGuid, java.naming.provider.url=ldap://DC1.contoso.local:389, java.naming.security.credentials=*****, java.naming.security.authentication=simple})
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5445 - Connected server with url:ldap://DC1.contoso.local:389
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createContext = javax.naming.ldap.InitialLdapContext@1caada7c
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering validateLDAPContext(ctx = javax.naming.ldap.InitialLdapContext@1caada7c, domainDN = DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5288 - Entering validateLDAPContext
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5300 - LDAP Search successful, context validated!!!
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5307 - Exiting validateLDAPContext
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting validateLDAPContext = true
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createContextForDomainConfig = javax.naming.ldap.InitialLdapContext@1caada7c
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting createDomainCtxMapFromDomainSetting = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@1caada7c}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getMembershipConnectionForDomainSetting = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@1caada7c}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getSearchControls(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1209 - Within getSearchControls()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>], name = searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>], name = searchScope, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = group.searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupsearchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getIntAttribute(name = searchCountLimit)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getIntAttribute = 0
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getIntAttribute(name = searchTimeLimit)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getIntAttribute = 0
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = searchReturningObj)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = searchDeferLink)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getSearchControls(objectType = group, options = null, scope = null, countLimit = 0, timeLimit = 0, returningObj = false, deferLink = false)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering resolveScope(scope = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting resolveScope = 2
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getAttrNames(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1624 - Within getAttrNames()
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getAttributesToRetrieve(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getAttributesToRetrieve(objectType = group, options = null)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemaAttributeNames(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = group, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemaAttributeNames = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getAttributesToRetrieve = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy]
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getAttributesToRetrieve = [cn, distinguishedName, owner, description, memberOf, objectSid, objectguid, mailNickname, GroupType, GroupScope, sAMAccountName, msDS-PrincipalName, managedBy, userAccountControl, msds-user-account-control-computed]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = revokeAttr)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1632 - Cannot fetch revoke information of user as no revoke attribute has been specified
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = lockAttr)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1645 - Cannot fetch locked information of user as no lock attribute has been specified
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1714 - Exitting getAttrNames()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getAttrNames = [Ljava.lang.String;@65d72e65
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getSearchControls = javax.naming.directory.SearchControls@7e195d7a
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1222 - Retrieved search control for group;scope:null;countLimit=0;timeLimit:0;deferlink=false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:1227 - Exitting getSearchControls()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getSearchControls = javax.naming.directory.SearchControls@7e195d7a
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@663b8efa[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@663b8efa[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getApplication()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getApplication = sailpoint.object.Application@663b8efa[id=8a8b80b3555b69f40155bde293cb6843,name=AD SingleTest]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2606 - Group membership attribute:member
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberSearchScope)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDNs()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getGroupMembershipSearchDn()
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = groupMemberSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDN, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = null
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchema(objectType = account, throwIfMissing = true)
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:122 - Entering getSchemas()
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchemas = [sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], sailpoint.object.Schema@2cdef0eb[id=8a8b80b3555b69f40155bde293db6846,name=<null>]]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.AbstractConnector:128 - Exiting getSchema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getSchemaConfig(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>], name = searchDNs, defaultToUnprefixed = true)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = account.searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = accountsearchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getSchemaConfig = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDn = [Ljava.lang.String;@308af0d8
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembershipSearchDNs = [Ljava.lang.String;@308af0d8
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2644 - Search string:(&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local))
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2650 - Searching in base:ou=users,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2651 - Search: (&(objectClass=Group)(member=CN=KG9999,OU=Users,DC=contoso,DC=local)) dn: ou=users,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getContextForDN(domainContextMap = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@1caada7c}, searchDN = ou=users,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = ou=users,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = ou=users,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering lookupDNFromDomainCtxMap(domainContextMap = {dc=contoso,dc=local=javax.naming.ldap.InitialLdapContext@1caada7c}, searchDN = ou=users,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = ou=users,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = ou=users,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting lookupDNFromDomainCtxMap = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:5471 - Unable to created LdapContext from DomainSettings
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting getContextForDN = javax.naming.ldap.InitialLdapContext@1caada7c
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2656 - Getting the context from _domainContextMap
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getCompositeName(baseDN = ou=users,dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getCompositeName = ou=users,dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2792 - Completed search
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@7a39b58f)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2815 - Exitting getGroupMembership()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getGroupMembership = null
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2063 - No entiltements found for AD
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2092 - Setting ResourceObject Uuid :{005c7753-6b14-4aca-81eb-48f3fa217480}
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2105 - Created resource object for identity:CN=KG9999,OU=Users,DC=contoso,DC=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:2110 - Exitting buildObject()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting buildObject = sailpoint.object.ResourceObject@264108ab
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering primaryGroupLookup(schema = sailpoint.object.Schema@16a8f09a[id=8a8b80b3555b69f40155bde293db6845,name=<null>])
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting primaryGroupLookup = true
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteArray(SID = S-1-5-21-2836116808-2396222863-416691703-495342)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@12877394
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 21)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@75ec4d2c
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2836116808)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@424e1bd3
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2396222863)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@6c644761
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 416691703)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@455682aa
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 495342)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@52c42201
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteArray = [B@60663b09
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering lookupPrimaryGroup(context = com.sun.jndi.ldap.LdapCtx@2e77272b, primaryGroupId = 513, userSid = [B@60663b09)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering buildPrimaryGroupSID(userSid = [B@60663b09, primaryGroupId = 513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@60663b09)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-495342
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2719 - USERS-SID: S-1-5-21-2836116808-2396222863-416691703-495342
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@5fc5b39d)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-0
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2728 - CHOPPED-SID: S-1-5-21-2836116808-2396222863-416691703-0
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2735 - REBUILT: S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting buildPrimaryGroupSID = S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteArray(SID = S-1-5-21-2836116808-2396222863-416691703-513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 5)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@2c62564e
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 21)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@7d8d8eb8
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2836116808)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@6a54a05d
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 2396222863)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@18ffafd1
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 416691703)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@26914aa6
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering longToByteArray(value = 513)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting longToByteArray = [B@37f8f882
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteArray = [B@7861f068
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToString(SID = [B@7861f068)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToString = S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:2277 - REBUILT-GROUP-SID: S-1-5-21-2836116808-2396222863-416691703-513
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering resolveDN(ctx = com.sun.jndi.ldap.LdapCtx@2e77272b, SIDBytes = [B@7861f068)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering SIDToByteString(sid = [B@7861f068)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting SIDToByteString = \01\05\00\00\00\00\00\05\15\00\00\00\48\b5\0b\a9\8f\75\d3\8e\f7\35\d6\18\01\02\00\00
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering getPrimarySearchDN()
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting getPrimarySearchDN =
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getAttribute(name = searchDNs)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getAttribute = [{groupMembershipSearchDN=OU=Groups,DC=contoso,DC=local, searchDN=OU=Users,DC=contoso,DC=local, searchScope=BASE, primaryGroupSearchDN=OU=Groups,DC=contoso,DC=local, iterateSearchFilter=(&(objectClass=person)(sAMAccountName=KG9999))}]
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = DC=contoso,DC=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering removeSpacesFromDN(strDN = dc=contoso,dc=local)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4904 - Enter removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:4919 - Exit removeSpacesFromDN
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:128 - Exiting removeSpacesFromDN = dc=contoso,dc=local
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:122 - Entering hasMore(enumeration = com.sun.jndi.ldap.LdapSearchEnumeration@1d855992)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getBooleanAttribute(name = useHasMoreElements)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getBooleanAttribute = false
QuartzScheduler_Worker-3 sailpoint.connector.LDAPConnector:128 - Exiting hasMore = false
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = primaryGroupSearchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:122 - Entering getStringAttribute(name = searchDN)
QuartzScheduler_Worker-3 sailpoint.connector.CollectorServices:128 - Exiting getStringAttribute = null
QuartzScheduler_Worker-3 sailpoint.connector.ConnectorException:104 - Entering <init>(t = java.lang.NullPointerException)
QuartzScheduler_Worker-3 sailpoint.connector.ConnectorException:110 - Exiting <init> = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:134 - Throwing resolveDN - sailpoint.connector.ConnectorException: NullPointerException
QuartzScheduler_Worker-3 sailpoint.connector.ConnectorException:104 - Entering <init>(message = Exception looking up primary group. sailpoint.connector.ConnectorException: NullPointerException)
QuartzScheduler_Worker-3 sailpoint.connector.ConnectorException:110 - Exiting <init> = null
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:134 - Throwing lookupPrimaryGroup - sailpoint.connector.ConnectorException: Exception looking up primary group. sailpoint.connector.ConnectorException: NullPointerException
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:1030 -
Exception occurred in reading primary group id attributes
sailpoint.connector.ConnectorException: Exception looking up primary group. sailpoint.connector.ConnectorException: NullPointerException
at sailpoint.connector.ADLDAPConnector.lookupPrimaryGroup(ADLDAPConnector.java:2286)
at sailpoint.connector.ADLDAPConnector.buildObject(ADLDAPConnector.java:992)
at sailpoint.connector.LDAPConnector.getObject(LDAPConnector.java:528)
at sailpoint.connector.ConnectorProxy.getObject(ConnectorProxy.java:380)
at sun.reflect.NativeMethodAccessorImpl.invoke0(Native Method)
at sun.reflect.NativeMethodAccessorImpl.invoke(NativeMethodAccessorImpl.java:62)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
at java.lang.reflect.Method.invoke(Method.java:498)
at bsh.Reflect.invokeMethod(Reflect.java:166)
at bsh.Reflect.invokeObjectMethod(Reflect.java:99)
at bsh.Name.invokeMethod(Name.java:858)
at bsh.BSHMethodInvocation.eval(BSHMethodInvocation.java:75)
at bsh.BSHPrimaryExpression.eval(BSHPrimaryExpression.java:102)
at bsh.BSHPrimaryExpression.eval(BSHPrimaryExpression.java:47)
at bsh.BSHCastExpression.eval(BSHCastExpression.java:60)
at bsh.BSHAssignment.eval(BSHAssignment.java:77)
at bsh.BSHBlock.evalBlock(BSHBlock.java:130)
at bsh.BSHBlock.eval(BSHBlock.java:80)
at bsh.BSHBlock.eval(BSHBlock.java:46)
at bsh.BSHTryStatement.eval(BSHTryStatement.java:88)
at bsh.BSHBlock.evalBlock(BSHBlock.java:130)
at bsh.BSHBlock.eval(BSHBlock.java:80)
at bsh.BshMethod.invokeImpl(BshMethod.java:371)
at bsh.BshMethod.invoke(BshMethod.java:267)
at bsh.BshMethod.invoke(BshMethod.java:195)
at bsh.Name.invokeLocalMethod(Name.java:917)
at bsh.Name.invokeMethod(Name.java:804)
at bsh.BSHMethodInvocation.eval(BSHMethodInvocation.java:75)
at bsh.BSHPrimaryExpression.eval(BSHPrimaryExpression.java:102)
at bsh.BSHPrimaryExpression.eval(BSHPrimaryExpression.java:47)
at bsh.BSHVariableDeclarator.eval(BSHVariableDeclarator.java:86)
at bsh.BSHTypedVariableDeclaration.eval(BSHTypedVariableDeclaration.java:84)
at bsh.BSHBlock.evalBlock(BSHBlock.java:130)
at bsh.BSHBlock.eval(BSHBlock.java:80)
at bsh.BSHBlock.eval(BSHBlock.java:46)
at bsh.BSHEnhancedForStatement.eval(BSHEnhancedForStatement.java:80)
at bsh.Interpreter.eval(Interpreter.java:664)
at bsh.Interpreter.eval(Interpreter.java:758)
at bsh.Interpreter.eval(Interpreter.java:747)
at bsh.util.BeanShellBSFEngine.eval(Unknown Source)
at org.apache.bsf.BSFManager$5.run(BSFManager.java:445)
at java.security.AccessController.doPrivileged(Native Method)
at org.apache.bsf.BSFManager.eval(BSFManager.java:442)
at sailpoint.server.BSFRuleRunner.eval(BSFRuleRunner.java:224)
at sailpoint.server.BSFRuleRunner.runRule(BSFRuleRunner.java:194)
at sailpoint.server.InternalContext.runRule(InternalContext.java:1166)
at sailpoint.server.InternalContext.runRule(InternalContext.java:1138)
at sailpoint.task.RuleExecutor.runRule(RuleExecutor.java:172)
at sailpoint.task.RuleExecutor.execute(RuleExecutor.java:113)
at sailpoint.api.TaskManager.runSync(TaskManager.java:794)
at sailpoint.scheduler.JobAdapter.execute(JobAdapter.java:127)
at org.quartz.core.JobRunShell.run(JobRunShell.java:202)
at org.quartz.simpl.SimpleThreadPool$WorkerThread.run(SimpleThreadPool.java:573)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering resolveAccountStates(obj = sailpoint.object.ResourceObject@264108ab, controlFlags = 512, computedControlFlags = 0)
QuartzScheduler_Worker-3 sailpoint.connector.ADLDAPConnector:122 - Entering getUserAccessControlMap()
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
I agree, Ryan, this looks like an exception in the core connector code. The stack trace is pretty telling with the NullPointerException in the sailpoint.connector.ADLDAPConnector.lookupPrimaryGroup() method looks like the root failure.
Please contact support for assistance here and reference this comment in the case notes.
--Adam

