- Products & services Products & services
- Resources ResourcesLearning
- Learning
- Identity University Get technical training to ensure a successful implementation
- Training paths Follow a role-based or product-based training path
- SailPoint professional certifications & credentials Advance your career or validate your identity security knowledge
- Training onboarding guide Make of the most of training with our step-by-step guide
- Training FAQs Find answers to common training questions
- Community Community
- Compass
- :
- Discuss
- :
- Community Wiki
- :
- Identity Security Cloud Wiki
- :
- How to Customize Identity Details for Certifications via REST API
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
How to Customize Identity Details for Certifications via REST API
How to Customize Identity Details for Certifications via REST API
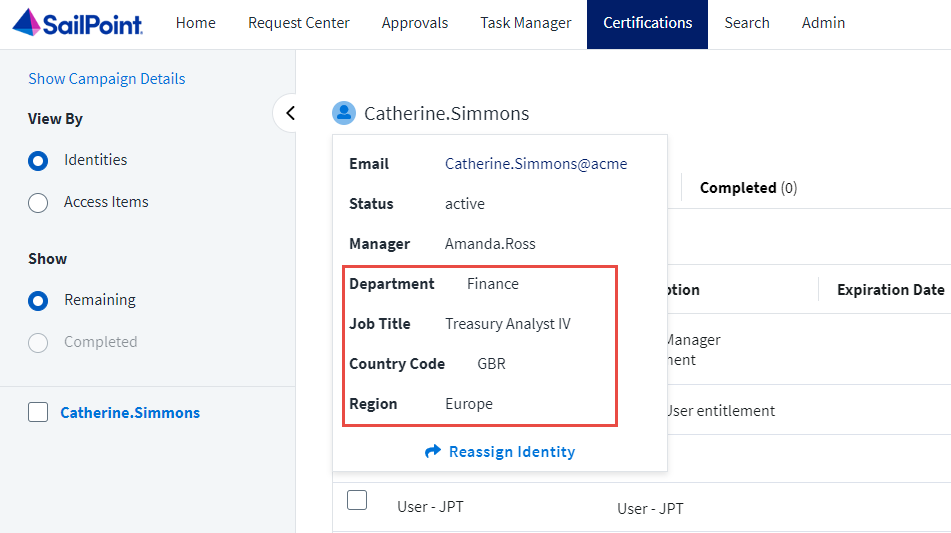
In order for reviewers to make the best informed decisions in certification reviews, it is helpful for the reviewers to be able to see specific information about the identities they are reviewing. Email, lifecycle state, and manager are shown by default, but it is often helpful to show other attributes such as department, title, region, etc. In this article, we will show how to configure up to five custom identity attributes on the identity details panel in certification reviews to assist the reviewer in the decision making process.
This configuration cannot be made in the IdentityNow user interface but needs to be done via REST API. You can use an API client like Postman or cURL for all API calls utilized in this process. Review this guide for information on OAuth 2.0 authentication for IdentityNow REST API calls.
Before we can make a configuration change to the public identity config, we need to get the current configuration. This is achieved by using the Get Public Identity Config API endpoint.
Run the following API call where {tenant} is your tenant name:
GET https://{tenant}.api.identitynow.com/beta/public-identities-configIf this has never been configured before, you should get a response like this:
{
"attributes": [],
"modified": null,
"modifiedBy": null
}If it has already been configured, your response will look like this:
{
"attributes": [
{
"key": "department",
"name": "Department"
},
{
"key": "title",
"name": "title"
}
],
"modified": "2022-09-02T23:22:07.400Z",
"modifiedBy": {
"type": "IDENTITY",
"id": "2c9180867624ce5b01762f370ea63c3d",
"name": "SailPoint Trainee"
}
}You can add up to five custom attributes. If you already have fewer than five configured, you can add more. If you already have five configured but you want to add a new one, you have to decide which one to replace.
To update the configuration, you will use the Update Public Identity Config API endpoint with a JSON response body containing the custom attributes. You must use the exact technical attribute name of the identity attributes, but you can configure a different display name.
Run the following API call where {tenant} is your tenant name:
PUT https://{tenant}.api.identitynow.com/beta/public-identities-configwith a JSON request body as shown below including an array of the attributes you want to add. "key" is the technical identity attribute name, and "name" is the display name you want to appear in the certification review:
{
"attributes": [
{
"key": "department",
"name": "Department"
},
{
"key": "title",
"name": "Job Title"
},
{
"key": "country",
"name": "Country Code"
},
{
"key": "region",
"name": "Region"
}
]
}If your call and request body were correctly constructed, you should expect a successful response of 200 and a response body that looks like this:
{
"attributes": [
{
"key": "department",
"name": "Department"
},
{
"key": "title",
"name": "Job Title"
},
{
"key": "country",
"name": "Country Code"
},
{
"key": "region",
"name": "Region"
}
],
"modified": "2022-09-02T23:44:37.414Z",
"modifiedBy": {
"type": "IDENTITY",
"id": "2c9180867624ce5b01762f370ea63c3d",
"name": "SailPoint Trainee"
}
}After configuring the public identity config as above, hovering over the name of an identity in a certification review shows the custom attributes:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Thanks for your post. Do you know, how can we remove default attributes 'email, manager and status ? I have tried above api and it seems it doesn't change any default attributes instead it adds new set of attributes with PUT request. I had added 5 attributes in the requests. On the UI, I could see 8 attributes. 3 default + 5 newly added.
Also can same api be used for removing default columns in view by 'Access Items' ? I want to remove 'manager' column from the 'Access Items' view before it is sent to reviewers.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
You are not able to remove the default attributes email, manager, and status. The manager column also cannot be removed from the 'Access Items' view.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Can we configure the Manager certification or something else to certify the user's AD account? If they have multiple AD accounts for any reason and manager can decide which AD account the user can keep and disable the other AD account.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
In the search interface, you can configure a search based certification of access on the AD source with a search query like this:
@access(source.name:"Active Directory")
source.name is, of course, the exact name of your AD source.
You can then choose manager as the reviewer.
If the identity has multiple accounts on the AD source, all the access items from all accounts will be included in the campaign.
There is no way to disable an account in a certification campaign, only revoke access that was granted by request.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Is it possible add the above attributes only for specific certification campaign means for specific source. Every one dont want this information but specific source team want see these attributes.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Any identity attributes added via the public identities config API will be global and viewable in all certification campaigns.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi @christina_gagnon is there a way to add custom columns in access review open tab in sailpoint identity IIQ
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Please post this question in the Compass IIQ forum or the Developer Community IIQ forum.