- Products & services Products & services
- Resources ResourcesLearning
- Learning
- Identity University Get technical training to ensure a successful implementation
- Training paths Follow a role-based or product-based training path
- SailPoint professional certifications & credentials Advance your career or validate your identity security knowledge
- Training onboarding guide Make of the most of training with our step-by-step guide
- Training FAQs Find answers to common training questions
- Community Community
- Compass
- :
- Discuss
- :
- Community Wiki
- :
- IdentityIQ Wiki
- :
- PolicyEngine-1-1.zip
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
PolicyEngine-1-1.zip
PolicyEngine-1-1.zip
- Purpose
- Requirements
- How to use
- Details
- Architecture
- PolicyRunner
- Account PolicyRunner
- GroupPolicyRunner
- PolicyCleanup
- PartitionedRule
- Utils
- partitionedPolicyImpactAnalysis.xhtml
- Update 1.1
Purpose
IdentityIQ does not allow for violations on objects other than Identities, and will only allow one PolicyViolation per Constraint. This Policy Engine allows you to generate any number of PolicyViolations for potentially any SailPointObject. I only have ManagedAttribute implemented, and it is specific to AD Groups, but the base is here.
Requirements
This PolicyEngine implements the PartitionedRule that is posted here https://community.sailpoint.com/docs/DOC-8968. This zip file does contain the PartitionedRule code, so you do not need to add it separately. But if you want information on the PartitionedRule you can follow the link above.
How to use
To use, you will need to add the code to your repository and update all the package locations accordingly. I highly recommend using the SSB (Services Standard Build) for this. Once you have everything hooked up, you need to create active Advanced Policies with active Constraints and point to Rules. The Rule may return more than one PolicyViolation and, if you tag your Policy correctly, you can generate PolicyViolations for ManagedAttributes. When you write a Policy for this Engine, IIQs Policy Engine will fail. This becomes obvious when you run LCM Provisioning where Running Policies is on by default. You will likely need to turn this off or limit the Policies that LCM Provisioning is using.
Details
Architecture
From the user perspective, you initiate the PolicyEngine by creating a TaskDefinition of the type “Partitioned Rule”. Fill in the options
- Object Class to run the Rule on: the SailPointObject that your Policy handles.
- Identity and ManagedAttribute are supported by this code.
- Rule: the Rule that will run the Policies.
- “Account Policy Runner” and “Group Policy Runner” are included in this code.
- “Account Policy Runner” runs on an Identity
- “Group Policy Runner” runs on a ManagedAttribute
- Rule Config: Comma separated list of Policies to run.
- Unlike the built-in Policy Refresh, this will still skip Policies that are disabled even if they are present in this list.
- If left empty this will run all the Policies for the Runner selected
- Debug Mode: true will do all the logic but not save the PolicyViolations. False saves the PolicyViolations.
- Unlike the “run simulation” button on the Policy page, a simulation from this task will run partitioned.
- Size of each partition: the size you want each partition to be.
- I have a limit of 100 total partitions hard coded so that you don’t accidentally run thousands of partitions.
I have 4 TaskDefinitions included a simulation and real a version of Account and Group PolicyViolations.
The user will also need to set up at least one Policy for the PolicyEngine to run on. You will need to use an Advanced Policy, and your Constraint will need to use the method “Rule” and point to a Rule object. Also, your Policy must have an argument called “policyType” added to it. The “policyType” is used to indicate which Policies are relevant to the Runners. This needs to be done from the Debug page or in code.
The Rule needs to be able to handle the SailPointObject you are passing it, but can return as many policyViolations you wish. The Runner will aggregate them together for reporting and saving. As a result of these changes, the simulation button from the Policy page may not work, and I suggest that they not be used for these Policies.
Assuming you are running “Account Check Active Policies,” the Partitioned Rule will split your Identities into partitions and will run each Identity on the “Account Policy Runner”. “Account Policy Runner” looks up the Policies that are tagged with the “policyType” of “account”. Once the engine has all the relevant policies, it will check if the Policy and the Constraint are active then extract the Rule from the Policy and run the Rule. The Rule will return a List<PolicyViolation>, and the Runner will do a diff and save the new PolicyViolations, delete the old ones, and return the aggregated data to Partitioned Rule to be displayed on the TaskResults page.
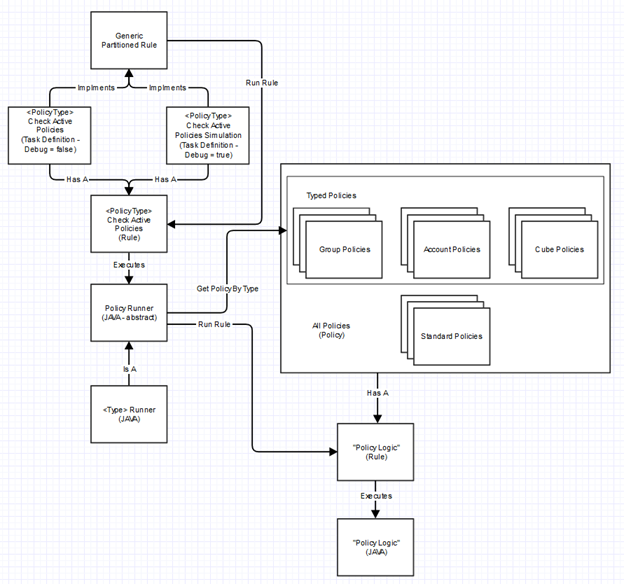
PolicyRunner
The core of the PolicyEngine. Coordinates what Policies need to run and aggregates the resulting PolicyViolations, diffs them, updates them, and returns the results to the Partitioned Rule.
Account PolicyRunner
Concrete implementation of PolicyRunner that runs on Identities. Can return more than one PolicyViolation.
GroupPolicyRunner
Concrete implementation of PolicyRunner that runs on ManagedAttributes. Can return more than one PolicyViolation and saves spadmin as the target for all of them.
PolicyCleanup
Required to cleanup Policies that are targeting non-Identity objects. For example, if you have a PolicyViolation on a group that was deleted you will need to run PolicyCleanup to delete the PolicyViolation.
PartitionedRule
Generic TaskDefintion and code to run any Rule on every SailPointObject specified. See https://community.sailpoint.com/docs/DOC-8968 for more info.
Utils
Just the common code that PolicyEngine uses
partitionedPolicyImpactAnalysis.xhtml
The xhtml page that allows you to see the results of the PolicyEngine. NOTE: you must update faces-config.xml for this to work without crashing the UI
faces-config.xml
I have included our file but you should take the last bean in the file and paste it into your faces-config.xml to ensure that you have all the configurations you need for your version of IIQ.
CollectedPolicyImpactAnalysis
This is used by partitionedPolicyImpactAnalysis.xhtml and mapped by faces-config.xml so that the UI page may render without brining the server down.
Known Issues/Weird Quarks
- Saving large amounts of Group PolicyViolations while partitioned sometimes causes an error. I believe this is because all of these PolicyViolations are saving to spadmin and we are getting consistency errors. This is only really an issue when getting a large number of PolicyViolations at once, like when you turn on the new Policy. These failures do not fail the whole workflow the individual Policy is skipped, and the error message is returned to be displayed on the TaskResults page. On following runs, they will work.
- Example: “Failed to save new PolicyViolation '<name>' with exception java.lang.RuntimeException: sailpoint.tools.GeneralException: Batch update returned unexpected row count from update [0]; actual row count: 0; expected: 1. skipping...”.
- If you are taking advantage of the additional features provided by this PolicyEngine the “run simulation” button on the Policy page will not work. You will need to use a task that has the Debug option set to “true” to run a simulation. This is weird because it is different but this simulation also runs partitioned, so it will reduce the amount of time it takes to get simulation results.
- We wrote almost all of our Policies with AD in mind and that each constraint will run on a single AD Application. I only mention this because you may need to edit things that don’t make sense without that context. For example, ManagedAttribute is assumed to be an AD Group there for we sometimes look for AD values like “cn”.
Update 1.1
- Fixed UI crashing issue by adding CollectedPolicyImpactAnalysis bean to faces-config.xml and updating partitionedPolicyImpactAnalysis.xhtml to use it. You only need the very last bean and you should copy IIQ’s excising faces-config.xml to paste the last bean yourself so that you have all the correct mappings for your version of IIQ.
- Fix a bug where PolicyViolation was not being removed for a Policy or a Target that was deleted by updating how the data structure works.
- Minor refactoring
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi,
cool, I assume the same principle will work for bundles as well. We have some constellations where a role composition is containing policy violations. That would be nice to show it independent of identities.
Regards
Martin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
You should only need to extend PolicyRunner for the SailPointObject you want to make a PolicyViolation for. Then make a TaskDefintion that will run the new PolicyRunner. I tried to make it pretty generic but I only have my usecases to work with so I cannot garentee that it will work with no other modifcation, but I think it will.
Let me know if you need any help.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi John,
thank you for the reply. I will let you know as soon as tested.
Martin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
curious if this worked for you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi,
no, actually the project focus slipped to other priorities. I will follow up as soon as this top comes back
Martin
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Content to Moderator
Hi, thois sounds great as it imlements exactly these two functionalities, that I'm missing:
1.) returning ,more than one policy violations per identity and constraint - due to thatlimitation, I've written my own beanshell code to store the multiple violation information in the description field, but that's limited to 4k length.
2.) partitioning the policy run
So I'll definitely give it a try.
My question: will it work on Sailpoint v8.3 and potentially 8.4 (as we will update begin of 2024) ?

