- Products & services Products & services
- Resources ResourcesLearning
- Learning
- Identity University Get technical training to ensure a successful implementation
- Training paths Follow a role-based or product-based training path
- SailPoint professional certifications & credentials Advance your career or validate your identity security knowledge
- Training onboarding guide Make of the most of training with our step-by-step guide
- Training FAQs Find answers to common training questions
- Community Community
- Compass
- :
- Discuss
- :
- Community Wiki
- :
- Identity Security Cloud Wiki
- :
- Best Practices: Bypassing Strong Authentication Questions During Registration
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Content to Moderator
Best Practices: Bypassing Strong Authentication Questions During Registration
Best Practices: Bypassing Strong Authentication Questions During Registration
Overview
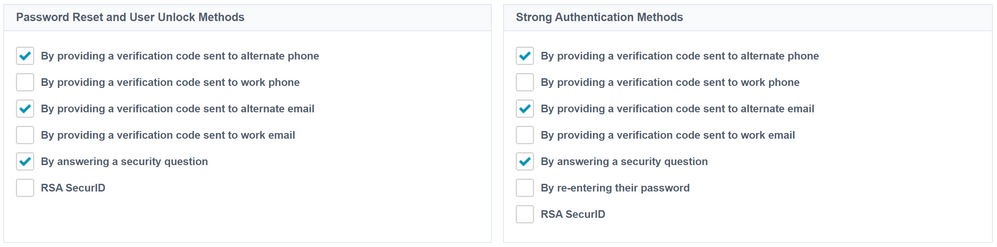
As part of the initial account claiming process with IdentityNow, users are sometimes asked to provide some registration information to help verify who they are when attempting actions like recovering forgotten passwords. This is part of the "strong authentication" configuration that IdentityNow administrators can set up for a given identity profile, as shown below:
Note that for both the Password Reset/User Unlock and Strong Authentication methods, at least one option must be selected.
While useful, this configuration can sometimes lead to confusion for end users, especially if their organization already leverages strong authentication elsewhere. Many identity providers already collect this information, and organizations who are using those providers for single sign-on (SSO) into IdentityNow actually do not need to leverage strong authentication with IdentityNow too.
Bypassing Strong Authentication Questions
As an IdentityNow administrator, you can specify which methods of strong authentication are permissible per your organization's security policy using the configuration pictured above. What is important to understand is that, if an option is marked as available for a user to choose during the strong authentication process, and IdentityNow does not already have the necessary information to complete that action, the user will be prompted for that information at the time of initial sign-in.
For example, if "By answering a security question" is checked, and the user has not selected their security questions and answers, they will be prompted to supply those upon login. Alternatively, if "By providing a verification code sent to alternate email" is selected and the user's identity already has an alternate email populated, they will not be prompted to supply it.
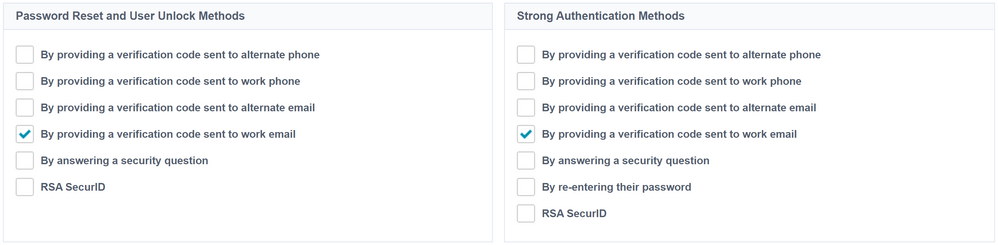
If you want to suppress all prompts for user information because you are leveraging a combination of multi-factor authentication and SSO elsewhere, the best practice is to select only options where you know the identity attribute underlying that method will always be populated. Because IdentityNow requires that all identities have a work email, the simplest way to accomplish this is to simply select "By providing a verification code sent to work email" for both the Password Reset/User Unlock and Strong Authentication methods, as below:
This configuration allows new users logging into IdentityNow to bypass registration questions, since the work email identity attribute is always populated.